Commvault Cloud Unity
The only cloud-native platform that unifies data security, identity resilience and cyber recovery at enterprise scale.

Platform Overview
The platform that powers the future of Resilience Ops
Commvault Cloud transforms resilience from a passive backup plan into an active operating model that helps enable the AI-driven enterprise. This is the future of ResOps: the new way to help secure, govern, and restore all your data, all the time.
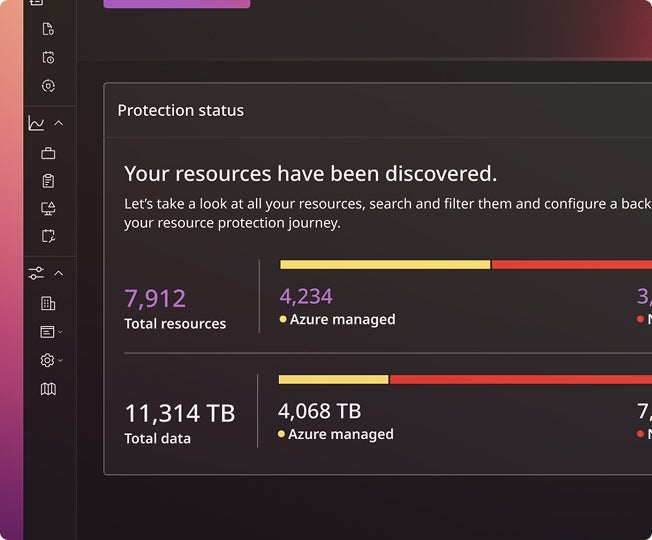
Discover more data, so you can act faster
Find and classify sensitive data across data, apps, and identities— giving you instant visibility into what matters most.
- Sensitive and PII data
- Cloud resources and configurations
- Native cloud snapshots and TCO analysis
- Identity access patterns
Secure and govern all your data, everywhere
Apply consistent policies for access, encryption, and retention. So protection happens automatically, across the business.
- Data access governance
- Remediation and redaction of sensitive data
- Air-gapped backup and retention policy enforcement
- eDiscovery and compliance
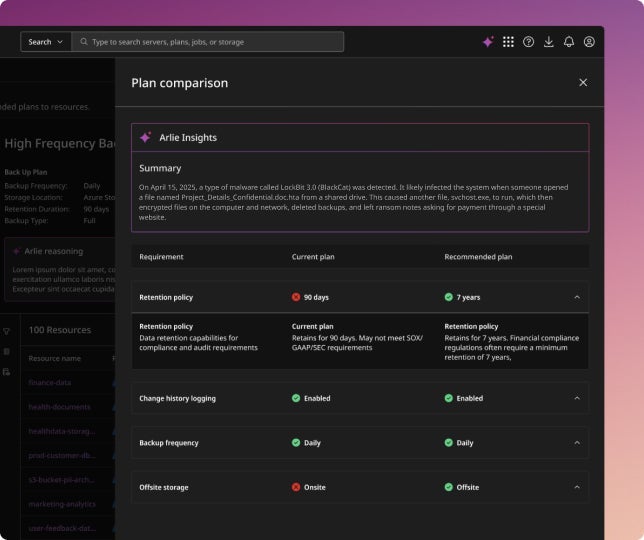
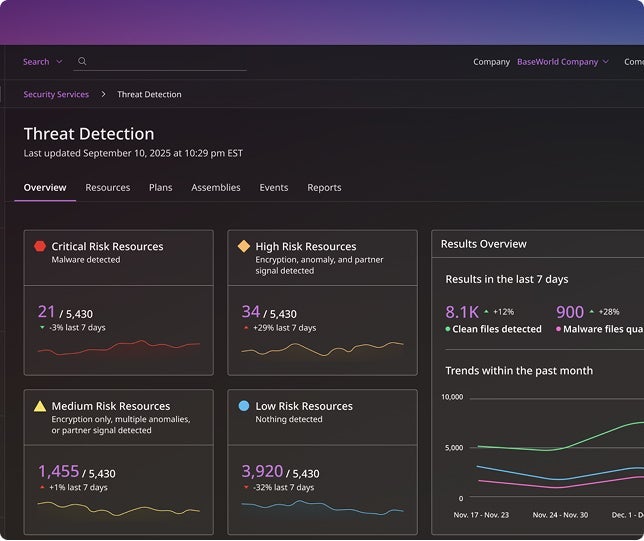
Leverage AI to stop AI-driven threats
AI-powered detection identifies unusual activity across data and identity systems, helping you stay one step ahead.
- AI-enabled threat detection and hunting
- Integrations with 3rd party threat databases
- Anomaly detection across identities, access and data
- AI-driven cleanpoint identification
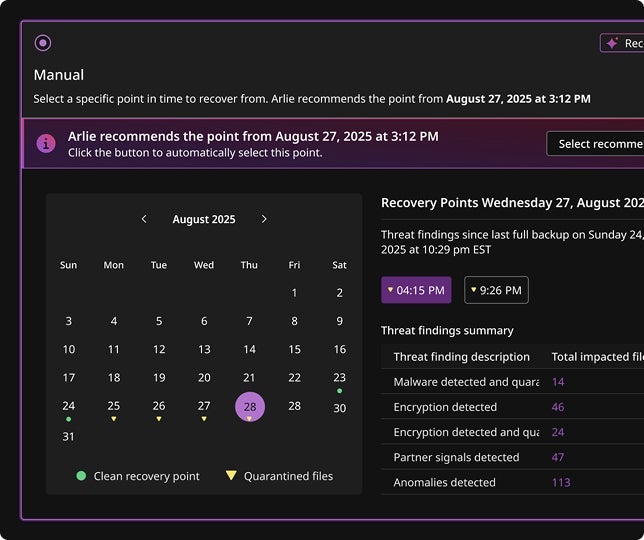
Recover your entire business in minutes
Commvault Cloud delivers the cleanest, fastest, most complete recovery of all your data, apps and infrastructure.
- On-demand cleanrooms for testing and forensics
- Full application and infrastructure recovery
- Granular and forest-level Active Directory recovery
- Enterprise-scale cyber recovery automation
Protected Workloads
One platform. All your data.
Commvault Cloud protects every workload that keeps your business running—from SaaS apps to AI stacks. One platform, total coverage, no compromises.
SaaS Apps
Safeguard business-critical platforms like Microsoft 365, Google Workspace, and Salesforce.
Learn moreActive Directory and Entra ID
Detect and recover from identity attacks with precision and confidence.
Learn morePlatform Architecture
Born in the cloud, built for the agentic enterprise.
Commvault Cloud Unity is intelligent, endlessly scalable, and seamlessly integrates with the tools you already use. Built on Metallic AI, our powerful automation engine.
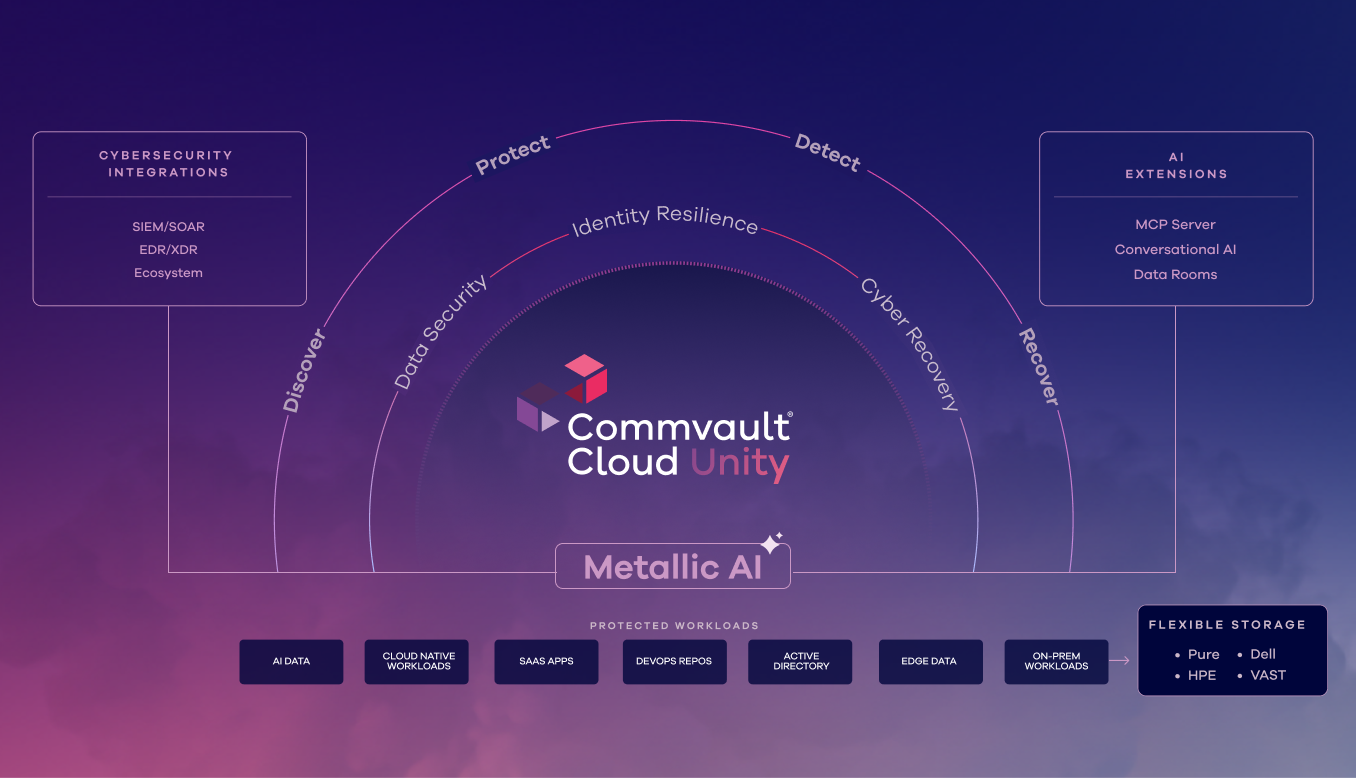
Metallic AI
The AI engine that powers automation and insight across the platform to enable the fastest, cleanest, most complete recovery.
Explore Metallic AIAI Integrations
Seamless connections with your security, identity, and cloud tools, turning fragmented workflows into one unified system.
Learn moreAI Extensions
Advanced capabilities like MCP Server and Data Rooms that extend resilience into your AI ecosystem.
Learn moreThe world’s most resilient companies depend on Commvault

Explore the Readiverse

Building AI on a Foundation of Resilience: A Pragmatic Playbook











