Anomaly Detection
Continuously monitor identity systems for unauthorized changes, privilege escalations, and unusual access patterns so you can mitigate identity-based attacks before they escalate.

HOW WE DO IT
Find hard to detect identity threats fast
Quickly identify unauthorized modifications, investigate suspicious behavior, and establish an accurate timeline of activity, enabling rapid threat detection and precision recovery.
Monitor and audit changes
Gain visibility into critical identity changes and activity that have been discovered.
Minimize risk and exposure
Pinpoint, investigate, and remediate suspicious activity to help minimize potential risk or disruption.
Minimize downtime
Quickly rollback unwanted changes to stop fast moving attacks in their tracks.
Real-time detection
Audit and remediate malicious changes fast
Commvault Cloud delivers real-time auditing and anomaly detection, helping to detect malicious identity changes in real-time and uncover hidden vulnerabilities before they’re exploited.

Real-time change auditing
Continuously monitor and track all security changes in Active Directory, with the details of who made them, when, and from where.
Anomaly alerts
Get notified of irregular and suspicious identity actions, such as unauthorized privilege escalations, unusual logins, and scope changes to Tier 0 assets, as they occur.
One-click rollback
Detect and rollback nefarious changes from the same view.
Visual threat timelines
Accelerate incident response by establishing an accurate timeline of activity, helping you to quickly determine when an attack began to select an optimal recovery point or roll back malicious changes to remove the artifacts of an attack.
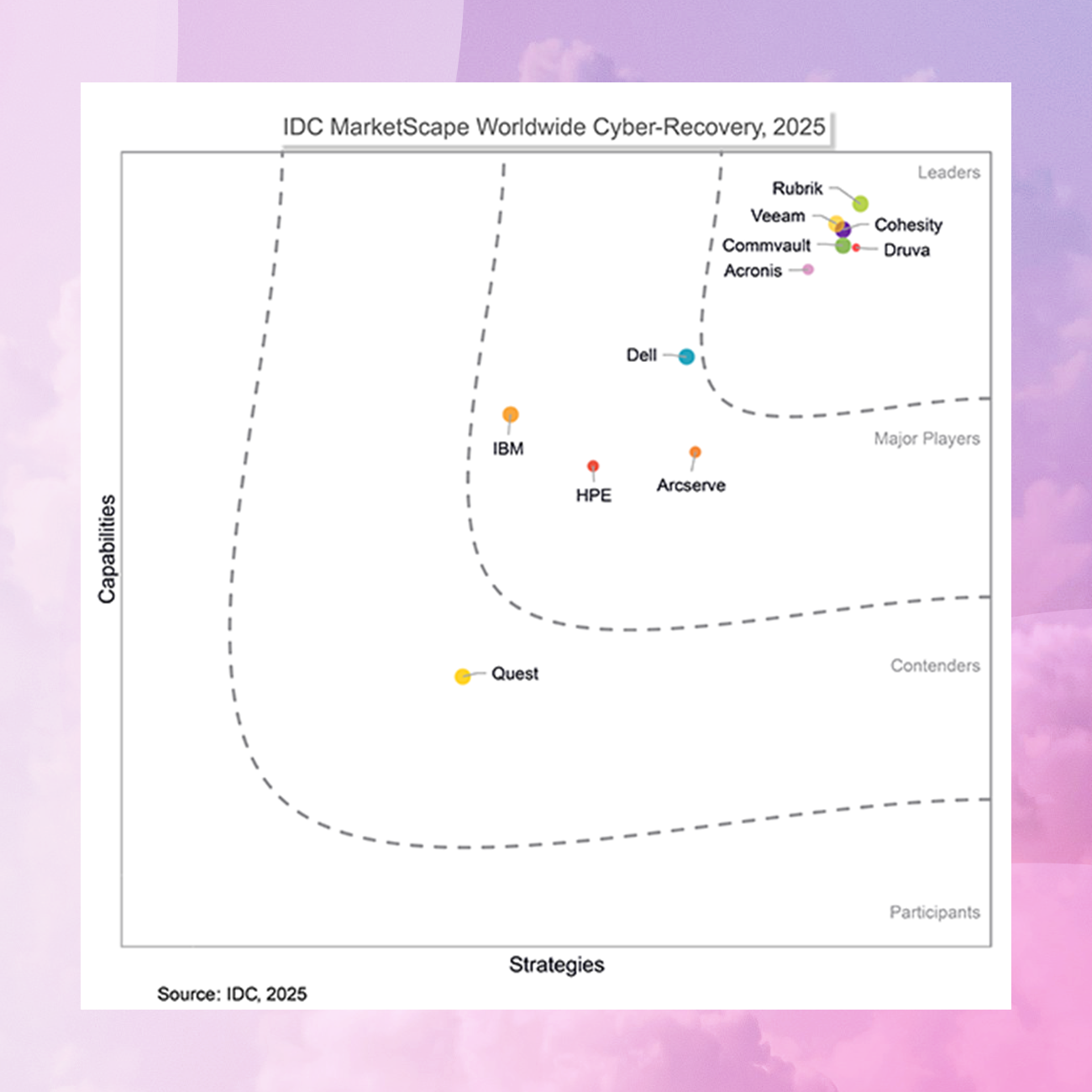
ANALYST REPORT
IDC MarketScape
Commvault named a Leader for strengths in cyber recovery architecture, workload and platform breadth, security ecosystem integration and dedicated cyber-resilience training.
Our Reach
Supporting more than 100,000 companies
eBook
Exposed: The Truth About Active Directory, Identity Resilience, and Rapid Recovery
Your organization’s identity infrastructure is under siege, and traditional backup and recovery methods are no longer sufficient. Learn why these approaches fall short and discover how you can build identity resilience with Commvault.


Securing the Core

Safeguard Microsoft AD and Entra ID Resilience and Recoverability

Identity Security Health Check
Frequently Asked Questions
Why is identity infrastructure a frequent target for attacks?
Identity systems are a prime target for attacks because they serve as a centralized gateway to multiple applications and services across the organization, making them a lucrative target for attackers seeking to gain broad access to sensitive information. By compromising an identity system, attackers can potentially obtain credentials or authentication tokens that grant access to numerous downstream systems, allowing them to move laterally within an organization’s infrastructure.
What is identity change auditing?
Identity change auditing continuously monitors and record modifications and authentication events across your identity systems, tracking who changed what, when, and where. This continuous approach provides real-time historical trail and alerts on suspect changes.
Why is monitoring Active Directory important?
Active Directory monitoring provides visibility into authentication patterns, privilege changes, and policy modifications that could indicate compromise.
Your ability to detect unauthorized changes to security groups, unusual authentication patterns, or suspicious account modifications can mean the difference between stopping an attack in its early stages and dealing with a full-scale breach. AD monitoring also supports compliance requirements by providing audit trails of administrative actions and access attempts.
Take the next step
We’re ready when you are
Resilience is a continuous journey. No matter where you are in your path, we’ll help you take the next step.