Keep Backup Data Clean
Recover and restore clean data quickly and avoid file reinfection by automatically quarantining suspicious or compromised data.

Demo Video
Commvault® Cloud Threat Scan
See how Commvault Cloud Threat Scan automatically scans backup files for malware, detects data anomalies, and enables fast, clean recovery.

How we do it
AI-enabled scanning to detect and stop threats
Active monitoring of backups, with automatic quarantining of infected or suspicious data, provides confidence that you can recover clean data quickly.
Smart quarantine
Infected files are automatically quarantined from the backup content and skipped during recovery.
Multi-layered file analysis
Our secure scanning uses a built-in signature-based malware engine, algorithms, and file comparisons to identify, label, and quarantine threats found within backups.
Advanced AI built-in
Leverage more than 100 million threat intelligence indicators to quickly identify new threats.
SIEM and SOAR integration
Alerts integrate with existing security operations tools like SIEM and SOAR platforms to jump-start investigations with added context.
Unknown threats, stopped
Spot next-generation polymorphic and shapeshifting malware.
Accuracy like you’ve never seen
Find threats with greater accuracy and reduce false positives.
THREAT SCAN FEATURES
Recover and restore clean data, automatically
Pinpoint and isolate compromised backup content like encrypted files, malware-infected virtual machines, or those with significant changes.
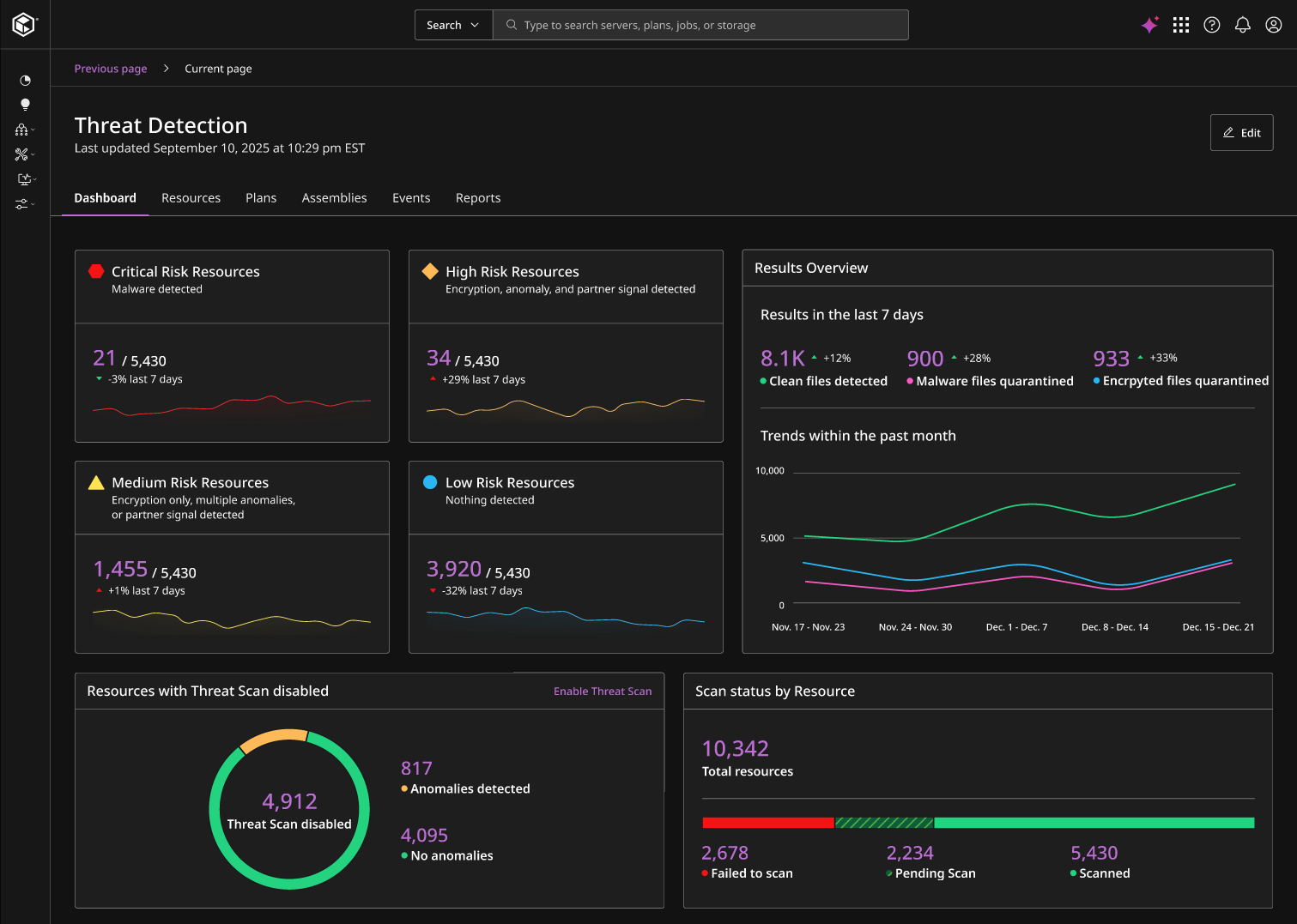
IDENTIFY BAD BACKUPS
Discover threats that live in backed up files
Spot compromised backups and automate responses with AI-driven encryption detection, malware detection , or files with significant changes.
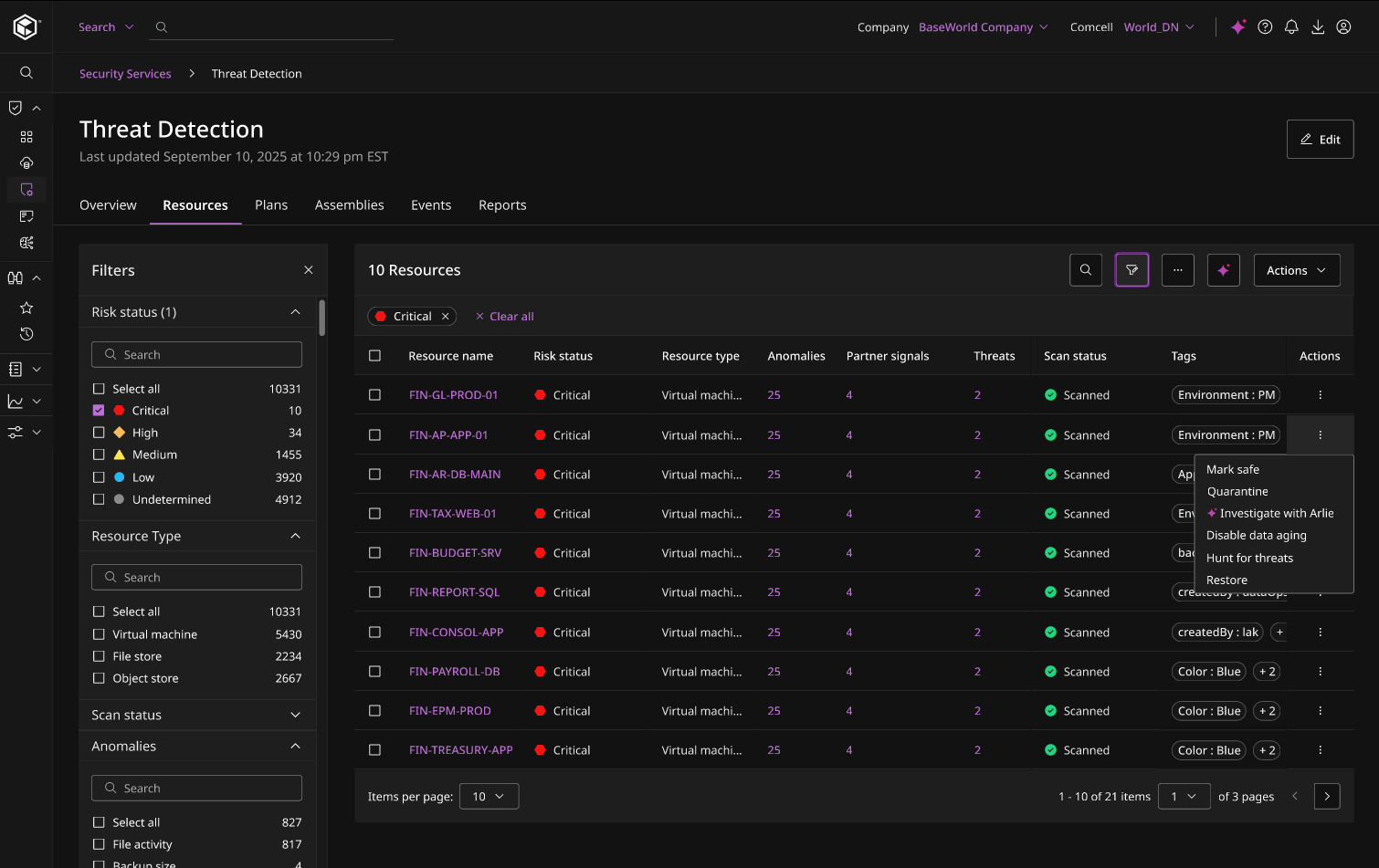
RECOVER CLEAN DATA
Prevent reinfection during recovery processes
Automated identification and assembly of the last known good version of your data while retaining, isolating, and quarantining bad data for forensic investigation.
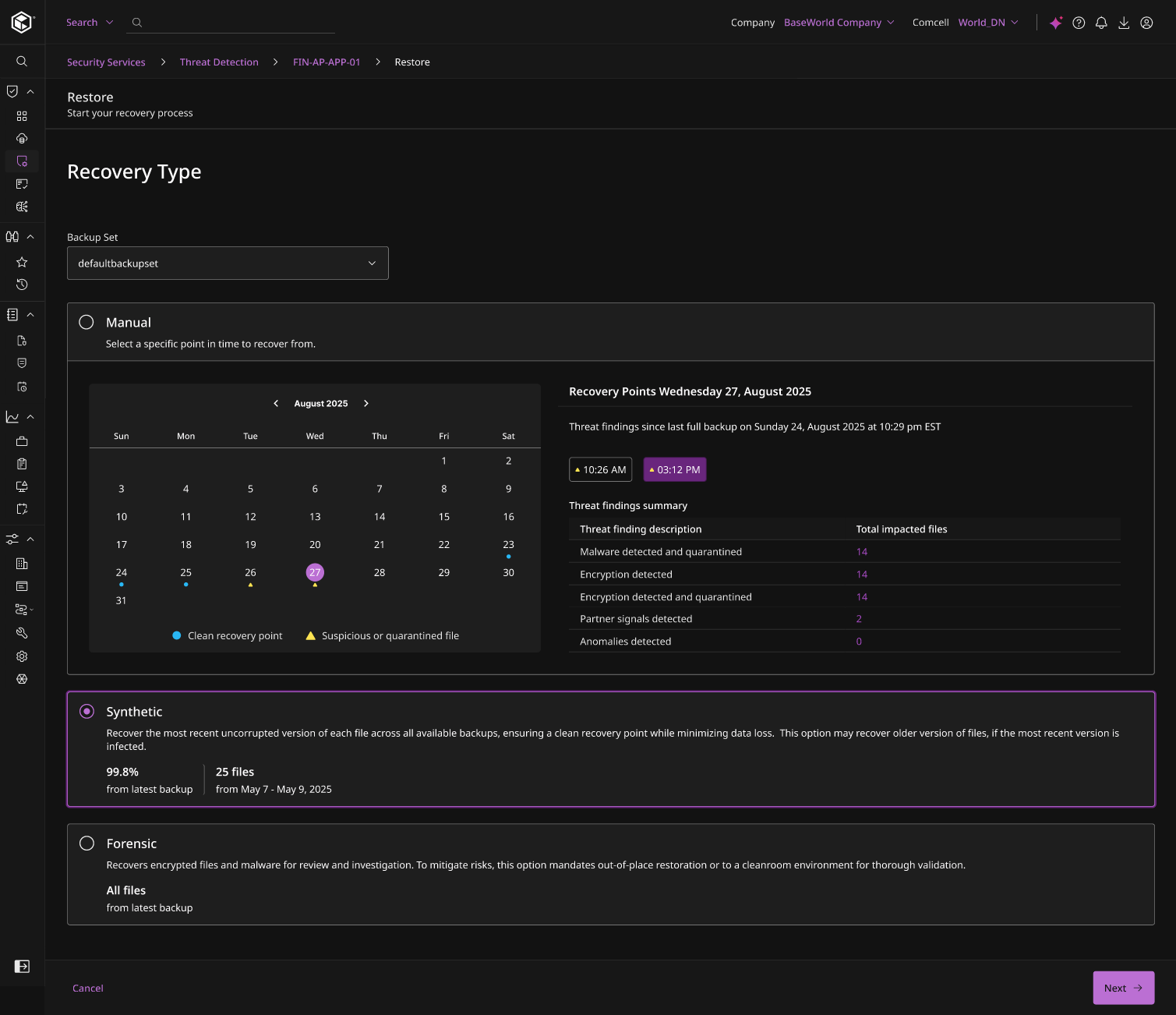
TEST RECOVERY DATA
Hunt for threats and validate your restore before going live
Find zero-day and never-before-seen threats and test your restore data in an isolated Cleanrooms before recovering into production sites.
Analyst Report
IDC MarketScape: Worldwide Cyber-Recovery 2025 Vendor Assessment
Commvault was recognized for strengths in cyber recovery architecture, workload and platform breadth, security ecosystem integration and dedicated cyber-resilience training.

Our Reach
Supporting more than 100,000 companies
Datasheet
Threat Scan datasheet
Enable swift and clean data recovery by analyzing backup files to find corrupted and encrypted data.


Ransomware recovery demo

Cyberthreat protection with resilience and recovery

Customers speak on strengthen threat detection
Frequently Asked Questions
How does Threat Scan prevent files from being restored?
Threat Scan analyzes files during the backup process, looking for malware signatures, encryption events/changes, or even suspicious changes over time (if the file has been backed up before). If a file exhibits any suspicious characteristics, it’s quarantined and prevented from being restored during a recovery process in production.
Do you keep a copy of suspicious or compromised files?
Yes. While we identify Cleanpoints so you can quickly restore only clean, good data to live environments, we also keep a copy of the suspicious file so your incident response or forensics team can analyze it in an isolated instance and determine its origin or the threat actor’s desired effects.
Why is Threat Scan more accurate than our existing signature-based threat detection?
To truly protect your data, you need more than static signatures. Commvault’s Threat Scan pairs traditional methods with advanced heuristics, behavioral analysis, the power of AI and machine learning, and telemetry correlation—plus integrations with leading security solutions. This layered approach helps you detect both known and unknown threats, exposes hidden or obfuscated malware, and surfaces Cleanpoints to enable you to recover clean data, fast.
How does Threat Scan integrate with security technologies?
Threat Scan can send alerts to anomalies or malware detection directly to your SIEM or SOAR tools, like Splunk, Palo Alto Networks XSOAR, or Microsoft Sentinel, enabling SecOps teams to get warnings that something may be wrong. We can also deliver suspicious files directly to a Sandbox system for further analysis or detonation.
Further, organizations can create a synergy between IT and Security teams by integrating signals from leading security tools within the Commvault Cloud Threat Detection and Response dashboard and unify visibility for accelerated incident response.