Cyber Recovery That Supports Your Resilience
Take control of your cyber resilience with Commvault Cloud and its AI-enabled capabilities that deliver rapid, clean recovery in the face of modern threats.

Demo Video
Cyber Recovery Demo Video
Commvault’s Cyber Recovery solution helps enable secure, isolated backup and rapid restoration of critical data in the face of cyber threats. By walking through key features like air-gapping, immutable storage, and cleanroom provisioning, it gives decision-makers a clear view of how to build resilience into their data protection strategy.
Unified Cyber Resilience
Recover trusted data with confidence
Commvault Cloud lets you quickly find your last-known-good backup with Cleanpoint™ identification and then verify recovery integrity to help you recover with confidence.
Restore your organization’s minimum viability
Commvault Cloud enables cyber recovery that prioritizes the clean recovery of the most critical business systems, apps, and data needed to maintain continuous business.
Recover clean data in a controlled way
Following a cyberattack, Commvault Cloud delivers the most important part of recovery—clean data and a clean, isolated environment to recover to.
Test your cyber recovery plans
Commvault Cloud lets you practice your recovery plans and validate that your recovery can be successful following an attack, all in a cost-effective, on-demand, isolated recovery environment.
Clean Data
Cleanpoint™ Identification
Easily go back in time and find your last-known-good data with Cleanpoint Identification and our AI-enabled threat detection that can quarantine compromised data and help prevent reinfection.

Easily pinpoint last-known-good files and VMs
Don’t leave your recovery to chance. Commvault Cloud uses AI-enabled threat detection to indicate your last-known-good backup so you worry less about recovering compromised data or risking reinfection during recovery.
Exclusive Synthetic Recovery™
With Synthetic Recovery™, you can help reduce the risk of rolling back good, clean data following a cyberattack by automatically creating a Synthetic Recovery assembly made up of Cleanpoint-identified files across multiple backups and timeframes.
Isolate compromised data for forensics
Gain helpful insights about malware by isolating known-bad files for forensic tear-down and investigation in a Cleanroom or isolated recovery environment.
Isolated Recovery Environment
Cleanroom Recovery™
Cleanroom Recovery™ delivers a fast, on-demand, cloud-based recovery environment for testing, cyber forensics, and recovery staging.

Test your recovery plans
Utilize a safe and isolated environment to test cyber recovery plans on demand.
Validate Clean Recovery
Use a Cleanroom to stage recovered files for observation, run additional threat detection, and check that data and applications are clean and working properly.
Safely investigate suspicious files & VMs
Use a Cleanroom as a recovery location for suspicious or compromised files for safe, isolated forensic investigations completely separate from production environments.
Find and isolate threats fast
Threat detection & threat hunting
Quickly and intelligently identify threats present in your protected data and VMs, and quarantine affected assets like files, objects, or VM images to prevent reinfection on recovery.

Fight modern attacks with AI-enabled detection
Quickly identify threats like malware, file encryption, and zero-day or polymorphic threats that are present in your protected data and VMs. Quarantine affected data or vms to prevent reinfection on recovery.
Intelligently hunt for threats
Integrate your existing security tools and your own threat intelligence, file hashes, or custom rules alongside commvault cloud detection technology to intelligently detect threats across your protected data.
Detect behavioral anomalies
Detect unusual user behaviors, such as impossible travel, and correlate anomalies across security tools for comprehensive threat analysis.
Analyst Report
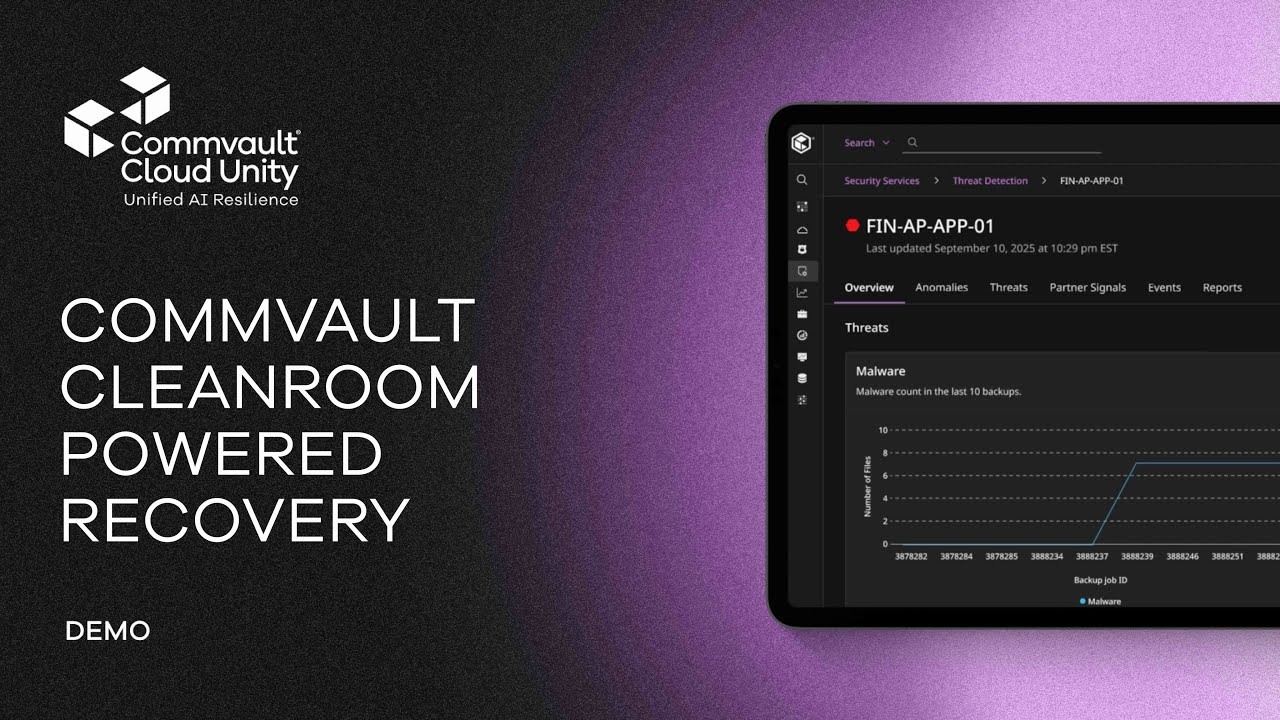
IDC MarketScape: Worldwide Cyber-Recovery 2025 Vendor Assessment
Commvault was recognized for strengths in cyber recovery architecture, workload and platform breadth, security ecosystem integration and dedicated cyber-resilience training.
Our Reach
Supporting more than 100,000 companies
WHITEPAPER
5 Ways Commvault is Changing The Game of Cyber Resilience
Explore five key ways that Commvault Cloud empowers organizations to become more cyber resilient, maintain operational excellence, and be a continuous business.


Cyber Recovery 101: Your Guide to Building a Resilient Cloud-first Enterprise

The Cyber Resilience Reckoning

From Discovery to Recovery: The Complete Cyber Resilience Solution in Minutes
Frequently Asked Questions
Why do I need dedicated backup and recovery solutions in an age of cloud-native tools?
Your organization needs to be confident that its data is readily available across the entire environment, whether on-premises, in the cloud, in multiple clouds, or hybrid environments. It’s all about availability and avoiding costly data loss scenarios.
- Point solutions have limited protection and create data silos
- Additional point solutions are often needed as your data infrastructure evolves, which creates even more segregated data silos
- Segregated data leads to inefficiencies, longer go-to-market cycles, and increased storage costs
- Quick, complete, cost-effective data access, protection, and recovery is critical for business planning and operation.
- A copy of your data should be stored outside of your own cloud account (air-gapped), or even in a different cloud.
How can I protect my data from ransomware, corruption, or accidental deletion?
Commvault Cloud is built upon a zero-trust framework, where data is air-gapped and isolated from source environments. In other words, Commvault Cloud stores backup copies in a separate security domain. That means data loss events that impact production data (such as user error or an internal attack) cannot also impact backup copies. With rapid and flexible restore options, you can quickly restore lost or compromised data.
How is disaster recovery different from cyber recovery?
Cyber recovery and disaster recovery both aim to restore operations after disruption, but they differ in focus and approach. Disaster recovery restores systems after events like natural disasters, outages, or hardware failures, emphasizing speed and availability through mirrored or replicated environments.
Cyber recovery, on the other hand, focuses on restoring clean, uncompromised data after cyberattacks such as ransomware, using isolated, immutable storage (like an air-gapped storage). While disaster recovery is typically managed by IT teams to resume normal operations quickly, cyber recovery involves both IT and security teams to validate, scan, and securely recover trusted data.
Why is it important to consider implementing “immutability” capabilities for backup data?
Implementing immutability capabilities helps keep your data safe from unauthorized changes. In the context of ransomware attacks, where attackers often attempt to encrypt or delete backups to force organizations into paying a ransom, this provides confidence that your backup data remains untouched.
Get Started
Try Commvault Cloud today
Cyber resilience for the cloud-first enterprise, with the first platform built to enable continuous business.