You need your backup data to be clean and recoverable and for your organization to have the expertise, resources, and knowledge on how to respond to a breach, cyber-attack, or disaster to maintain business continuity. You cannot afford to wait for an incident to occur to figure out how your organization will respond and determine what to do during a security incident. According to Rob Joyce, director of the US National Security Agency’s cyber security arm, the rest of the world should take the Russia-Ukraine war to heart and learn how Ukraine has learned to keep its critical infrastructure online and running1.
There’s a lot riding on the health of your data environment to reduce the impact of a cyber attack and ensure you have a quick, curated recovery if you are attacked. Are you taking the proper steps to ensure that your data is protected? Have you protected your backups through immutability and air gap? Do you have an incident response plan where team members understand their roles and responsibilities? Are your overnight backups completed properly and recovery ready for business continuity?
The way you think about recovery matters.
Standardization – for Recovery Readiness

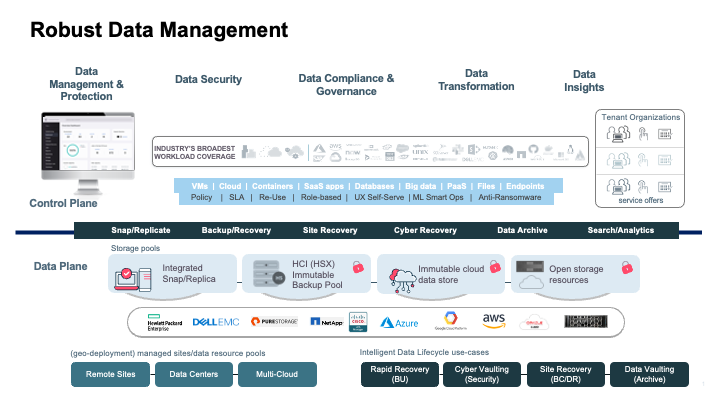
Modernizing your data protection capabilities is important to avoid a slow and complicated recovery. It’s equally crucial to meet the requirements for reporting and compliance. Given the scope of this potentially time-consuming job, you also need to make effective use of automation, APIs, artificial intelligence, and machine learning. And to make optimal decisions about your recovery priorities, you need complete visibility and data insights across your environments, from on-premises to multi-cloud.
Point solutions for each of the data scape footprints, such as cloud, endpoint devices, SaaS, and on-prem can potentially slow down the ability to make the recovery a seamless experience for the organization. Standardizing on a data protection suite that can give you a bird’s eye view of the entire estate and manage recovery SLAs from a single dashboard is the need of the hour and helps your organization be recovery ready.
Protect What Matters Most
Be confident that your data is readily available across any environment, whether it’s on-premises, in the cloud, in multiple clouds, or in hybrid environments. Access and visibility across your entire landscape are essential to identify and monitor unusual activity, protect your data wherever it may live, seamlessly migrate data as necessary, gain a comprehensive view of every location where your data is stored, and help you maintain IT agility to meet SLAs across your environments.
Commvault® Backup & Recovery provides enterprise-grade protection and recovery of virtual machines, containers, databases, applications (including cloud), endpoints, and files. Gain increased visibility and role-based access control to enable self-service, restricting unauthorized access while helping to eliminate data sprawl. Reduce the burden on database administrators while increasing their efficiency and allowing them to focus more on critical business activities.
Cyber and Disaster Recovery
Whether the damage is done by a natural disaster, hardware failure, data breach, or ransomware attack, you need to recover your data quickly with zero data loss and as minimal downtime to business as possible. While the characteristics of cyber and disaster recovery differ, the outcome remains the same: recover clean data quickly. Many perceive cyber recovery as another form of disaster recovery – the methodology of recoveries is similar, using data protection and recovery tools like Commvault, but the salient difference is that in cyber recovery use cases, the validity of data is in question and performing application validation frequently and performing scrubbing of data before restore to production is critical to avoid any risk of reinfection. To learn more click here.
You want simplification and automation to enable effective disaster and cyber recovery across your complex environment. The ability to quickly revert to the last good point of recovery and perform restores rapidly is key for a successful recovery.
Robust Data Protection for Successful Recovery
- Flexibility to perform disaster and cyber recovery to the cloud at scale – If your primary environment becomes unavailable, what are you going to do? Have the ability to failover to cloud capacity temporarily without the need to provision and pay for a persistent secondary data center.
- Predictable operating costs through the cloud for reliable disaster and cyber recovery – Anticipate the cost of cloud operations when recovering data across cloud workloads by easily backing up data and replicating it to execute recovery efforts across regions.
- Secure data across clouds for quick disaster and cyber recovery – Enhanced data security with encryption at rest and in flight coupled with tight role-based access controls are core requirements for securing access to data; Support for immutable object locks, combined with logically air-gapped repositories with network segmentation ensure that the data-protected copies are safeguarded from malicious actors and malware from wreaking damage, – finally, integration with privileged access management (PAM) and enhanced identity and access management (IAM) tools along with external key management platforms to manage and control keys, help elevate the overall security posture of the data protection landscape and assure security of the copies from malicious data access.
- Align with ZTA – Zero Trust architecture is vital to your company’s security posture and plays an important role in securing your data-protected copies, as these data-protected copies of your application are the insurance policy to help your organization recover in the event of a crisis.
There is a clear understanding across the industry today that there is no single solution that can render an environment one hundred percent ZTA compliant – instead, there is consensus that Zero Trust architecture is an architectural philosophy that requires all the applications in the estate to abide by the principle of “Verify first, trust after.”
It provides the foundations for micro-segmentation of the IT landscape, access limited with the Least Privilege principle, and all communication to and between the micro-segments being authenticated, audited, and verified2. The underlying philosophy for zero trust is never assume trust, but continuously validate trust, so bad actors don’t get in.
Ransomware Recovery
The strength of a successful recovery starts very early in the planning, strategizing, and implementation stages of securing the environment, followed closely by a well-rehearsed validation and drill exercises that are tested as frequently as possible.
The last thing you want to do when contending with a high-pressure attack is to waste time figuring out which data needs to be recovered and in what order. Building blocks for a Zero Loss Strategy begin your recovery efforts with the following elements under the broad strokes of Proactive and Reactive steps. (While proactive is not the same as preventive, we can never with complete certainty prevent a cyber-attack but take the appropriate measures to protect data and ensure we can effectively recover from it with minimal downtime and zero data loss.)
Proactive: Identify and Protect
- Use a centralized management console – A single interface that provides the capability of driving business SLAs with a top-down approach to data protection and disaster recovery initiatives. This helps minimize complexities and provides thorough visibility.
- Air gap ready – Have an immutable, logically air-gapped copy to ensure that protected data is cybersafe. Include tight role-based access controls (RBAC), network segmentation, and encryption of data in flight and at rest. Engage the power of privilege access management solutions.
- Authentication, Authorization, and Auditing – Ensure user access is continuously validated and monitored. Leverage security controls such as multi-factor authentication and multi-person authentication to add the necessary checks and balances to your data protection platform.
- Foundational hardening – Make sure that your data protection solution includes industry-leading CIS Level-1 benchmarks to reduce the surface area of attack.
- Replication – Replicate your backups to an alternate site to ensure you have a recovery target.
Proactive: Monitor
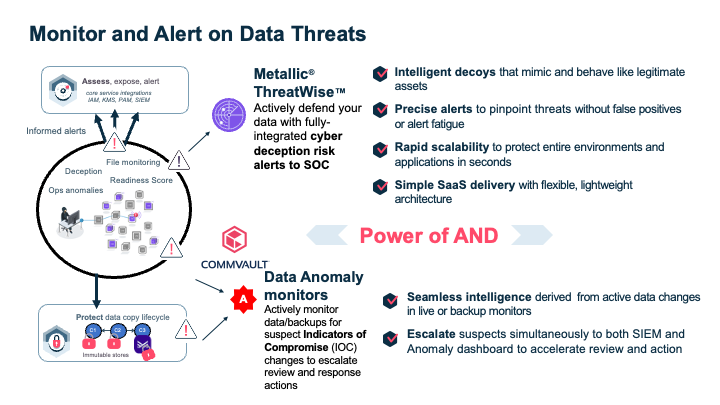
- Anomaly detection – Get early warning alerts of potential attacks and use analytics to monitor your data landscape. A quick response can help quarantine the malware and reduce the overall blast radius of the attack and thereby minimize downtime and mitigate data loss.
- Early proactive warning – Incorporate early warning with cyber threat detection technology to ward off bad actors before they infiltrate.
Proactive: Respond
- Data Validation – Validate backups frequently to detect corrupted backups early in the cycle so that you can maintain your Recovery Point Objective SLA and not reinfect your environment while performing recoveries. Enterprises are now investing in network segmented, clean rooms to validate data on a regular cadence. To build confidence in your recovery readiness and avoid surprises at the time of an actual event, perform application validation of your data every 30-45 days.
- Recovery Validation – Consider implementing cyber recovery drills not just on the data recovery elements but also around key decision makers and IT department(s). Create a RACI matrix of stakeholders and points of contact for public relations, legal, finance, and IT.
Reactive: Recover
- Recovery Orchestration – One-click recovery of a clean copy of workloads to production after validating and sanitizing recovery points.
- Rapid restoration – Accelerate recovery by streamlining operations with automation and standardized processes to ensure business continuity.
- Recovery Forensics – Analyze backups through custom tools and perform forensics securely in isolated networks so you don’t cause reinfection.
- File Data Analysis – Detect files that may be encrypted or corrupted by malware to ensure you are not backing up infected files.
- Threat Analysis – Detect malicious content of the backed-up data – inline at the time of restore to ensure you are not risking reinfection of production systems while restoring from the last good point-in-time on backups.
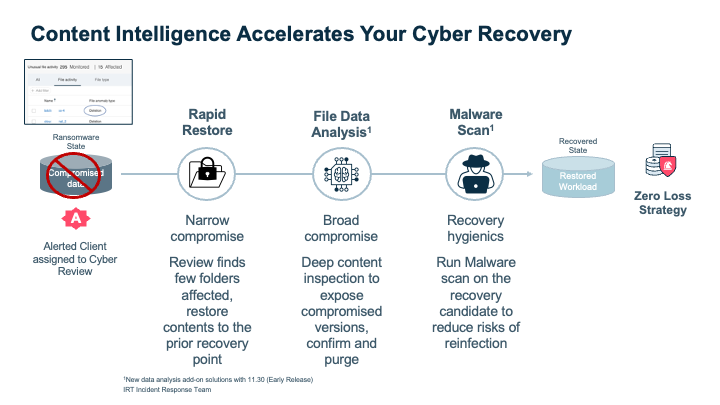
When data has been encrypted by a hacker, paying the ransom might not be enough as most times the decryption keys may not work as expected, or the process of decrypting large data sets may be time-consuming. To avoid data loss and minimize disruption, your best bet is to have a ransomware recovery strategy in place that can deliver fast, automated recovery.
A Zero Loss Strategy for Data Protection and Recovery
The right product and services are essential to be implemented effectively to ensure swift recovery from cyber events, and it starts with a strategy to better plan and manage the data protection landscape to minimize the impact on business. Successful restores are critical to the survival of the business. Introducing a Zero Loss Strategy, built on zero trust principles and implemented through a multilayered security framework for consistent and automated data protection and recovery, which are front and center for an environment’s recoverability and recovery assurance. The foundational areas of a Zero Loss Strategy consist of:
- End-to-end data visibility – Catch threats before they fully impact your data. With a single management platform, identify business-critical and sensitive data, reduce your attack surface, and minimize risk exposure.
- Broadest workload protection – Protect what matters most. Commvault covers the broadest of workloads, from traditional on-premises to hybrid cloud and SaaS applications; we also support native cloud integration, so as your organization and data grow, we can easily help you scale.
- Faster business response – Speed and accuracy are essential to responding to a ransomware attack. Consolidating your data protection to a single dashboard, the Commvault Command Center™, gives your organization greater production and efficiency.
An effective strategy is the foundation for a full and speedy resumption of normal operations. You need a new approach to data protection and recovery.
Incident response plan
Defending against ransomware is a major challenge – and no individual team can combat it on their own. Are your teams prepared?
With so many ransomware factors, it is usually within the innocent context that someone simply clicks a link, infecting an organization’s entire network with malware. Defending against ransomware is a major challenge, and even with the right products, services, and strategy, you need to ensure your entire team is on board, as no single team can combat an attack on their own. It takes a well-equipped, prepared, and practiced village to deal with complex threats successfully – one that includes:
- People – Being aligned with internal and external teams before, during, and after a ransomware attack is vital for speed and recovery so you can react faster and mitigate the costs associated with downtime.
- Process – It is important that internal and external teams are aware of and in sync regarding their responsibilities and what processes they need to follow during a ransomware attack. Test, test, and test your process, as speed will be essential, and you don’t want to test out your process during an attack.
- Technology – Follow the National Institute of Standards and Technology (NIST) Cybersecurity Framework to aid your preparation. Adopting a multi-layered security framework helps ensure your data is ready for recovery and reduces the risk of loss.
Please read our eBook Understanding Team Roles & Responsibilities in Fighting Ransomware to learn more.
Recovery Assurance
Integrations with security ecosystem tools like SIEM, SOAR, and PAM help to build your organization’s cyber resiliency and recovery assurance. Your data protection and recovery plan and elements are bolstered with built-in security capabilities of hardened components and monitoring, leveraging an automation framework.
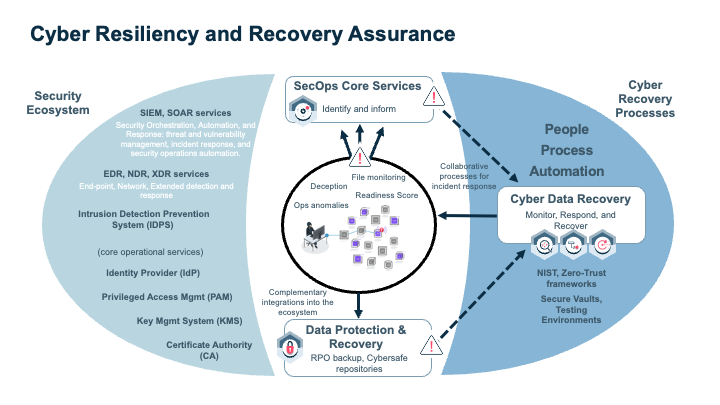
Simplify Recovery
You need an easy, efficient way to handle your recovery from all types of cyber or disaster situations. A single point of control lets you consolidate and streamline your recovery strategy across on-premises data centers, public clouds, and private clouds with consistent, strategic data management practices. Actionable insights help you verify that you can meet the RPOs and RTOs defined in your SLAs as well as regulatory requirements.
Determine how prepared your organization is for a ransomware attack. Take the Commvault risk assessment to find out.
Learn more about Commvault API integrations to improve your own data management platform and employee experience.
References
1. The Register, Jessica Lyons Hardcastle, Why a top US cyber spy urges: ‘Get religion on backups’, April 2023 – 2. Commvault, Vidya Shankaran, Ransomware Defense in Depth – Best Practices for Security and Backup Data Immutability, October 2021


