How are you protecting your data from a ransomware attack or natural disaster? What is your recovery plan? Is your disaster recovery plan the same as your cyber recovery plan? The steps you take to protect your data might be the same, but your recovery efforts may vary. Both types of disasters could be devastating to your business, but what’s critical is recovery. The average cost of downtime for large enterprises is more than $11,600 per minute,1 and 40-60% of small businesses won’t reopen after data loss.2 So, the way you think about recovery matters.
- What is a Cyberattack/ Natural Disaster/ Disaster Recovery/ Cyber Recovery?
- How do Cyber Recovery and Disaster Recovery Differ?
- What is an Incident Response Plan
- What Are the Types of Cyberattacks?
- How does Ransomware Spread
- How Commvault Fights Ransomware
- Ransomware Security Measures
What is a Cyberattack?
Gartner defines a ransomware attack as “cyber extortion that occurs when malicious software infiltrates computer systems and encrypts data, holding it hostage until the victim pays a ransom.”3 A cyberattack is very different from a natural disaster attack. In this instance, your data is intentionally infiltrated. Bad actors have proactively gained access and placed malware into your environment, locking up your systems, hijacking critical data, and seeking ransom. It is estimated that a ransomware attack occurs every 11 seconds.4
What Is a Natural Disaster?
When a disaster strikes, such as a flood, earthquake, fire, or storm, your data environments are inadvertently shut down or even destroyed. In this instance, your data is not intentionally infiltrated. In 2021, there were 401 natural disaster events worldwide.5
What Is Disaster Recovery?
Disaster recovery is the ability to regain access and functionality of critical data systems and IT infrastructure as soon as possible after a natural disaster occurs. It relies upon the replication of data from an off-premises location or cloud environment, where the data is backed up and not impacted by the natural disaster. In a disaster recovery situation, the goal is to restore business operations efficiently with minimal downtime and zero data loss, as the business readiness of the data is considered pre-qualified for recovery. In a disaster recovery situation, your efforts are centered on the efficiency of restoring operations.
What Is Cyber Recovery?
Cyber Recovery aims to provide the ability to regain access and functionality of critical data systems and IT infrastructure as soon as possible after a cyberattack such as ransomware occurs. In a cyber recovery situation, your objectives are to get your business backup and running from an air-gapped and immutable copy of data, which assures you of data integrity. Data protection solutions with the implementation of zero trust architecture assure you a layered approach to defense even for your backup environment. However, “seeing is believing” and this is where it is important to ensure you are frequently validating the business-readiness of the data as part of the cyber recovery tabletop exercises. This can be achieved by performing application validation of the data using custom scripts in a network-quarantined sandbox environment. By doing so, you can prevent any potential re-infection of the environment and thereby contain the “blast radius” after an attack.
How do Cyber Recovery and Disaster Recovery Differ?
Cyber recovery and disaster recovery differ. With disaster recovery, the focus is on the Mean Time to Recovery (MTTR) of operations and the smooth functioning of business. In a best-case disaster recovery scenario, data is not compromised. As for cyber recovery, it is all about your business survival, focusing on data, applications, infrastructure and more.
Characteristics of Disaster Recovery vs. Cyber Recovery
| Disaster Recovery | Cyber Recovery | |
|---|---|---|
| Principle requirement | Rapid means to recovery of business operations with minimal downtime. It is typically assumed that there is zero data loss. | Rapid recovery of business and its data, with zero data loss, and the assurance that data has not been manipulated or tampered with. |
| Recovery objective expected | Recovery to the closest point in time. | Recovery to the closest point in time from an air-gapped immutable copy. |
| Tools used | Typically requires replication tools to aid data replication between sites and locations, complete with orchestration to aid seamless failover and failback operations | Requires a host of tools and processes to confirm data has not been manipulated for the protection of applications, networks, use of SIEM/SOAR ecosystem solutions for forensics & analytics, and network monitoring tools. |
| Frequency of testing recovery runbook | Typically, once every six months to a year. | As frequently as possible to validate the business readiness of data. Exercises include processes that engage incident response teams (IRT), legal, corporate, public relations, communications, third-party insurance, and IT teams. These tabletop exercises help minimize downtime during times of crisis so that it becomes collective muscle memory when it comes to recovery. |
What Is an Incident Response Plan?

Do you have an incident response plan? Is your organization and its employees prepared for a ransomware attack or natural disaster?
All the teams involved must be able to play their part in the cyber recovery process effectively
They must be capable of exercising plans and have permission to execute those plans if something happens. During an actual attack, you don’t want teams pointing fingers at each other regarding who is responsible for what. This is often referred to as “IT Collision,” which can significantly impact an organization’s ability to respond to a cyber-crisis efficiently. Ensuring that all the key stakeholders and teams are enabled with the right permissions ensures that they can make swift decisions with authority – and this can be achieved by teams typically being given pre-authorization to perform prescribed actions. Process-induced latency to the recovery exercise can be eliminated without having to get people out of bed and onto a Zoom call to receive authorization.
As for C-Level executives, are your business leaders in sync? How many different business units and partners need to be involved in an incident response plan? Are you concerned about consequences to shareholders in the event of a ransomware attack?
- It is important that executives drive a business impact analysis of the entire estate that includes PPT (People, Process, and Technology) to measure the overall impact of downtime after a cyber event.
- Identify what needs to be part of the cyber recovery plan .
- Identify teams that need to be engaged with as security teams, IRT’s (incident response teams), cyber insurance partners, and data protection teams, as all need to work in close concert for the cyber recovery exercise to be effective.
- Detailed processes need to be chalked out that need to be followed during a ransomware attack.
- Finally, practice, practice, practice until it becomes collective muscle memory to be able to respond with minimal friction points during actual crisis response.
What Are the Types of Cyberattacks?
It is easy to assume that all ransomware is similar, and it is not uncommon to think that one size fits all in terms of prevention and preparation. However, because each type of ransomware is usually developed to attack different, targeted networks, they can be very different in the way they operate. It is essential to understand the different types currently being used (keeping in mind that attackers are capable of combining multiple types of ransomware).
The strength of protection against any ransomware attack is in your defense strategy, especially given the rise in zero-day vectors with no known tactics, techniques or procedures (TTP).
Six types of Ransomware:

CryptoWall – is responsible for a high percentage of ransomware attacks. Typically, CryptoWall is used to attack targets through phishing emails. The WannaCry ransomware virus is a derivative of the Crypto family and was at the core of the largest cyberattacks ever perpetrated. Unfortunately, the creators of CryptoWall continue to release new versions designed to get around security protections.
Locky – as the name implies, Locky is what it does (locks you out of files and replaces the files with the extension .lockey). However, its name misses the most damaging part of this type of ransomware – its speed. Locky has the distinction of spreading to other files throughout the network faster than other ransomware strains.
Crysis – takes data attacks to a new level, actually kidnapping your data and moving it to a new virtual location. The significance of this aspect of the attack is that it qualifies as a breach if your company works with personal data; organizations must contact anyone who may have information on your network to stay in compliance with local, state, and federal guidelines.
SamSam – attacks unpatched WildFly application servers in the internet-facing portion of their network. Once inside the network, the ransomware looks for other systems to attack.
Cerber – attacks the database server processes to gain access instead of going straight after the files. Its creators sell the ransomware software to criminals for a portion of the ransom collected, i.e., Ransomware-as-a-Service.
Maze – is a variant of ransomware representing the trend in what is called “leakware.” After data is encrypted, bad actors threaten to leak ransomed private data on the dark web unless the ransom is paid.
Safeguarding against ransomware must be at the forefront of organizations’ security efforts.
How Does Ransomware Spread?

Social Engineering is a key tactic used by cybercriminals to encourage unsuspecting users to download/click a spurious link/website. Ransomware is often spread through email phishing messages containing malicious links or by drive-by downloading, which occurs when a user unintentionally visits a contaminated site, and malware is downloaded onto the user’s computer or mobile device. Once within the IT environment, threat vectors move laterally within the network until detected. The anatomy of a ransomware attack is typically to move through unstructured data to remain undetected for as long as possible. Until recently, malware and threat vectors have been known to gestate within an environment for up to 300 days while gradually encrypting data sets and wreaking widespread havoc.
However, with more recent attacks, we find threat vectors being able to sweep in and achieve instantaneous, large-scale destruction by performing mass deletes or encryption. The speed of these attacks does not allow teams to respond fast enough. Therefore, ensuring that the data protection environment is safeguarded from day one against any pace of attack is key. Security professionals must rely on “air-gapped and immutable” backup copies as their insurance policy.
How Commvault Fights Ransomware
Commvault data protection and recovery can be a valuable part of your anti-ransomware strategy. Commvault multi-layered security is built on zero trust principles and based on the National Institute of Standards and Technology (NIST) cybersecurity framework to protect data and enable quick recovery in the event of a ransomware attack. Commvault helps protect and isolate your data, provides proactive monitoring and alerts, and enables fast restores. Advanced technologies powered by artificial intelligence and machine learning, including honeypots, make it possible to detect and provide alerts on potential attacks as they happen so you can respond quickly. By keeping your backups out of danger and making it possible to restore them within your Service Level Agreements, you can minimize the impact of a ransomware attack so you can get back to business right away (and avoid paying expensive ransoms).
Protecting and isolating your backup copies is critical for data integrity and security. Therefore, Commvault has taken an agnostic approach to immutability. With Commvault, you do not need special hardware or cloud storage accounts to lock backup data against ransomware threats. If you happen to have Write-Once, Read Many (WORM)-, object lock- or snapshot-supported hardware (which Commvault fully supports), you can still use Commvault’s built-in locking capabilities to complement and layer on top of existing security controls. Commvault’s ability to support layered defense for securing data sets against ransomware ensures that our customers benefit from a sound cyber recovery-ready architecture. Here are some elements to include in your immutability architecture:
- Access locks to isolate copy store against ransomware
- Immutability with lifecycle locks to reduce risks, balanced with consumption impact
- Air-gap isolation network and controls
- Configuration governance to protect against intentional or accidental changes
- Concurrent Recovery performance – reduce latency with due importance to speed and cost impact
- Automatic patching to stay current, simplifying management and maintenance of data protection infrastructure
- Alignment with the 3-2-1 data protection philosophy (3 copies of data, 2 different media, 1 vaulted copy)
Learn more about Commvault’s immutable infrastructure architecture here.
Commvault Multilayered Security Protection
With every environment having a mix of different infrastructures, securing backup data against random unauthorized changes can seem challenging. Just like securing your house, you need to identify the risks and enable the protection and monitoring capabilities to match your needs.
Many experts recommend having a layered anti-malware and ransomware strategy. Commvault has built these security capabilities into our data protection software and policies without the incremental management overhead. The Commvault data protection and management platform include five security layers:
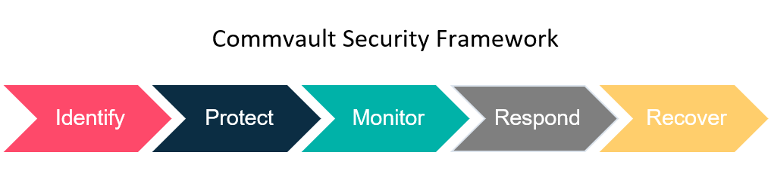
- Identify and mitigate risks to backup data within a single interface
- Protect by applying security controls based on industry-leading standards
- Monitor for ransomware, insider threats, and other threats
- Respond and take action on threats and continuously validate backup data
- Recover data quickly across multiple on-premises, cloud, and hybrid environments
Commvault multi-layered security consists of feature sets, guidelines, and best practices to manage cybersecurity risk and ensure data is readily available. It is essential to understand that these capabilities are part of Commvault’s core platform experience, Commvault Complete™ Data Protection. There is no special licensing, no additional costs, and no required hardware or software. The layered security depth is enhanced through greater integration with Metallic™ and Commvault HyperScale™ X for those customers seeking the simplicity of Backup as a Service or a data protection appliance, respectively.
Ransomware Security Measures

Air gap: Traditionally, air-gapped networks have absolutely no connectivity to public networks. Tape is a traditional medium for air-gapped backups because tape can be removed from the tape library and stored offsite. To air gap secondary backup targets on disk or cloud, some access is needed, but communication is severed when it is not required. When the isolated data does not need to be accessed, communication is severed either by turning communication ports off, disabling VLAN switching, enabling next-gen firewall controls, or turning systems off.
Multi-factor Authentication (MFA)6: This is a layered approach to securing data and applications where a system requires a user to present two or more credentials to verify a user’s identity for login. MFA increases security because even if one credential becomes compromised, unauthorized users will be unable to meet the second authentication requirement and will not be able to access the targeted physical space, computing device, network, or database.
Least Privilege Access: This standard security practice provides access to users and/or accounts with the bare minimum capabilities to do their job and nothing more. You decide who has access to what. This minimizes exposure if the account is compromised and limits data access leaks.
Perform Regular Backups with Immutability: Consider increasing the frequency of backups and expanding your data protection to a 3-2-1 backup strategy; 3 copies of your data, on 2 different media types, with a copy offsite and preferably air-gapped. Other essential data protection tools include encryption, write once, read many (WORM), and strict access controls.
Data immutability: Data that cannot be altered. To better protect against ransomware, ensure backup copies are immutable by using layered security controls, write once read many (WORM) capabilities, and immutable storage, as well as built-in ransomware protection for backup data.
Data encryption and key management: A technology in which data is translated into an unreadable form or code, and only users with access to a secret key or password can read it. Encryption at rest and in-flight ensures the backup data, even if exfiltrated, is rendered useless to bad actors without the decryption keys or password.
Anomaly Alerts: These indicate deviation from the expected pattern of data or events. Anomaly detection helps provide behavioral insight, giving your organization the ability to learn about identification patterns to understand your environment and recognize unusual behavior before a threat impacts your environment and business.
Honeypots7: A network-attached system set up as a decoy to lure cyberattackers and detect, deflect and study hacking attempts to gain unauthorized access to information systems. The function of a honeypot is to represent itself on the internet as a potential target for attackers — usually, a server or other high-value asset – and to gather information and notify defenders of any attempts to access the honeypot by unauthorized users.
Application hardening8: A catchall term for protecting an app against intrusions by eliminating vulnerabilities and increasing layers of security. Data security involves multiple layers of defense that are not limited to the app itself: the host level, the operating system level, the user level, the administrator level, and even the physical level of the device all have vulnerabilities that a good security system must address. For this reason, application hardening might be called system hardening or OS hardening as well.
Whether you are hit with a cyberattack or face a natural disaster — the reality is your organization needs to be prepared and take steps to protect your data and work with a provider who offers rapid cyber and disaster recovery solutions. So how prepared are you? Read our eBook on Understanding Team Roles and Responsibilities in Fighting Ransomware.
References
1.,2. Branko K: Web tribunal: 15+ scary data loss statistics to Keep in Mind in 2022, March 2022. – 3. Gartner, 6 Ways to Defend Against a Ransomware Attack, by Manasi Sakpal, November 2020 – 4. Safe at Last, 22 Ransomware Statistics to Help Fortify Your Cybersecurity Models: Jan 2022 – 5 Statistica, Madhumitha Jaganmohan, Global Number of Natural Disasters Events 2007-2021, February 2022 – 6. CISA – 7. TechTarget, Ben Lutkevich, Casey Clark, Michael Cobb, honeypot (computing) – 8. Thales, Application Hardening


