Identity Rollback & Threat Remediation
Rapidly restore compromised or misconfigured identities to a last-known good state, minimizing risk and downtime.

Demo video
Identity Resilience
Discover how Commvault Cloud simplifies finding and reversing unauthorized identity changes to help address active identity-based attacks in their tracks.

Rollback identity changes
Stop identity-based attacks in their tracks
Gain real-time insight to identify and quickly reverse unauthorized changes, privilege escalations, and accidental misconfigurations before they cause damage.
Reverse accidental changes
Undo accidental modifications in users, groups, and roles, restoring user accounts to a trusted state.
Neutralize active threats
Identify and roll back malicious changes quickly, locking out attackers and containing the threat before it escalates.
Minimize service downtime
Accelerate incident response with one-click rollbacks and clear audit trails. Know who made what change and when, enabling swift, precise remediation.
Real-time change auditing and rollback
Detect and remediate threats
Spot and reverse unauthorized changes in Active Directory from a single view. Proactively minimize downtime and contain threats before they escalate.

Real-time change auditing
Continuously monitor and track all security changes, providing detailed visibility and audit trails for every modification, deletion, or login event in Active Directory.
One-click rollback
Gain granular visibility into events, including who made changes, when, and from where, providing the necessary information to quickly roll back unwanted changes.
One-click rollback of changes
Identify and roll back harmful changes in one click from a single, unified view, restoring your environment to a known-good state.
Individual and bulk rollback
Undo changes to individual objects and attributes or in bulk—to any point in time.
Visual threat timeline
View the details of every security-related change and revert unwanted changes to remove the artifacts of an attack.
Reporting and audit trails
Support compliance requirements by providing audit trails of administrative actions and access attempts.
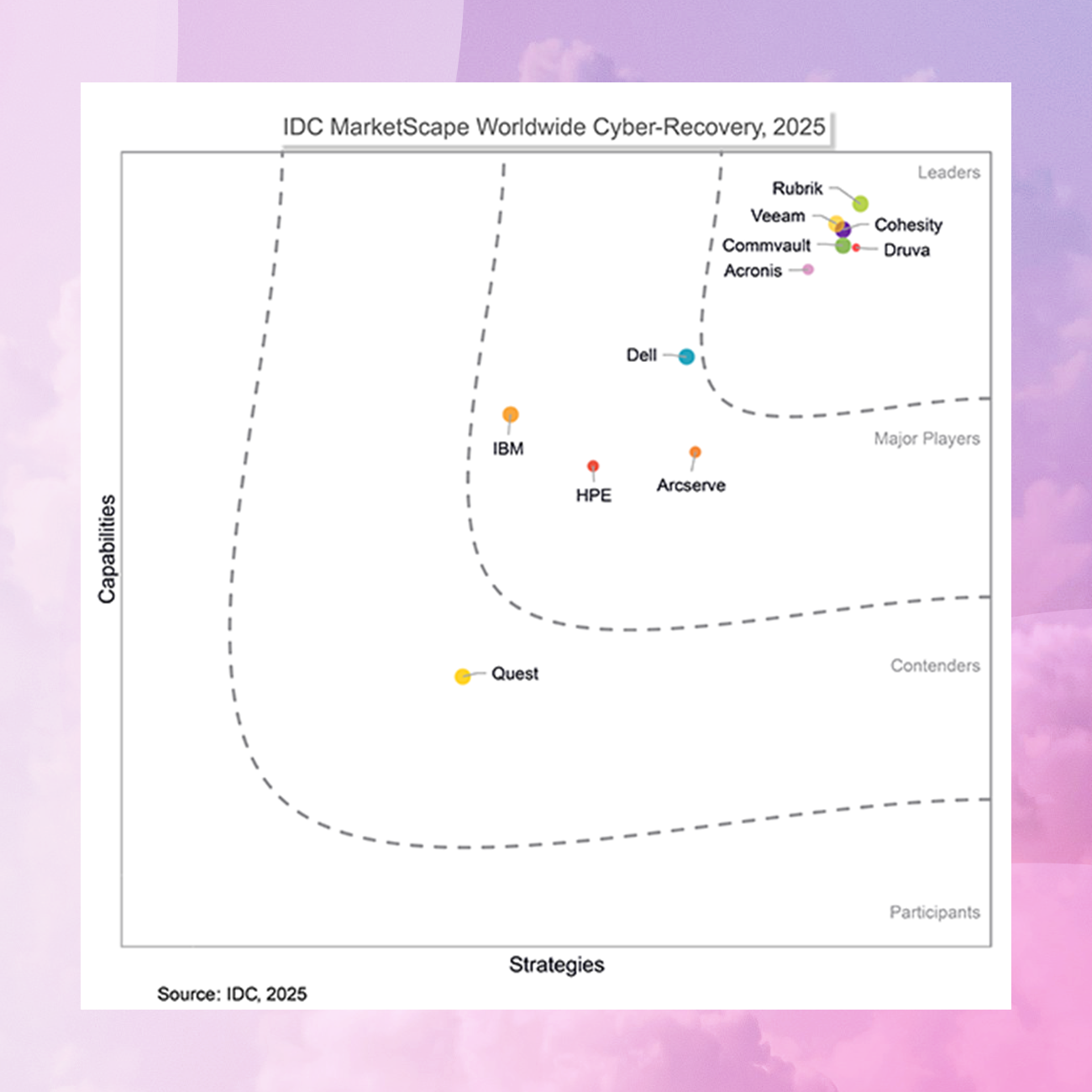
ANALYST REPORT
IDC MarketScape
Commvault named a Leader for strengths in cyber recovery architecture, workload and platform breadth, security ecosystem integration and dedicated cyber-resilience training.
Our Reach
Supporting more than 100,000 companies
eBook
Exposed: The Truth About Active Directory, Identity Resilience, and Rapid Recovery
Your organization’s identity infrastructure is under siege, and traditional backup and recovery methods are no longer sufficient. Learn why these approaches fall short and discover how you can build identity resilience with Commvault.


Safeguard Identity Resilience and Recoverability

Commvault Cloud Identity Resilience

Securing the Core
Frequently Asked Questions
What identity systems does this support, and what kind of changes can be rolled back?
Real-time auditing and rollback is supported for Active Directory. Commvault Cloud goes beyond simple user accounts to allow the rollback of changes to security groups, permissions, Group Policy Objects (GPOs), and other critical configuration attributes, providing broad protection across your hybrid identity infrastructure.
Can I roll back a single incorrect permission change, or do I have to restore the entire object?
You have forensic-level control, with a detailed, event-by-event timeline of every modification. From this timeline, you can choose to roll back a single change—like an accidental privilege escalation on one account—or select multiple malicious changes from an attacker and reverse them all in one bulk action. This precision enables you to only undo what’s necessary without impacting legitimate changes.
How does this assist with our compliance and audit requirements?
It provides a searchable audit trail of every change made within your identity environment. You can generate reports to demonstrate who made what change, when, and what the values were before and after to satisfy audit requirements for change control and data integrity.
Take the next step
We’re ready when you are
Resilience is a continuous journey. No matter where you are in your path, we’ll help you take the next step.