Backup Everything, Everywhere – and Recover Clean Data Faster
Commvault® Cloud provides data availability and business continuity across your entire data estate – from a single unified platform.
Overview Video
Commvault® Cloud Platform
Commvault Cloud powered by Metallic AI® is the first platform for true cloud cyber resilience, delivering the highest security, most intelligence, and fastest recovery.

Back up data and recover all workloads and environments
Data disruption impact
Reduce downtime. Keep operations moving. Discover how Commvault’s comprehensive platform drives data resiliency across apps, clouds and data centers at the lowest TCO.
30%
The average outage results in direct revenue loss of 30%.1
40%
More than your data is at risk—40% of disruptions also damage a brand‘s reputation.2
82%
Of organizations experienced at least one unplanned downtime incident ub a 3-year period.3
References
1Trili, The True Cost of Downtime: 21 Stats You Need to Know, August 2022. 2Trili, The True Cost of Downtime: 21 Stats You Need to Know, August 2022. 3Sundeep V. Ravande, Forbes, Unplanned Downtime Costs More Than You Think, February 2022.
Introducing
One platform for cyber resilience everywhere
Protection for your hybrid world – from a single-pane-of-glass.
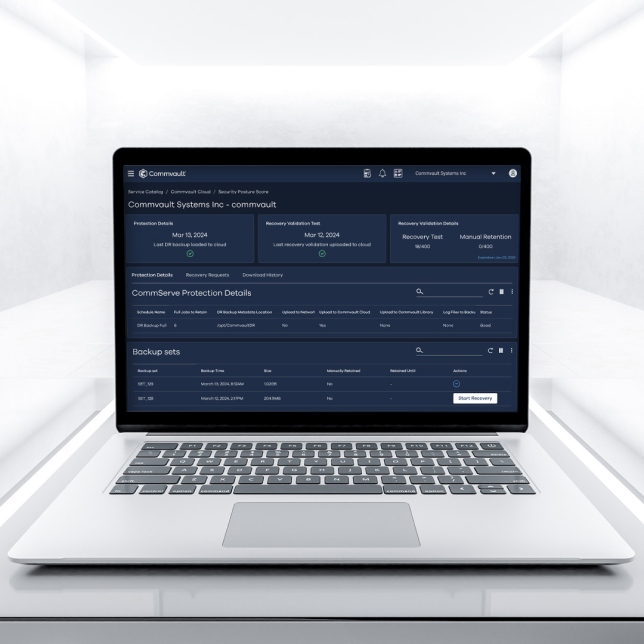
For SaaS & the edge
Protecting SaaS app data is your business’s responsibility. But you don’t have to do it alone. Commvault’s SaaS is FedRAMP High Authorized and delivers proven protection for distributed and remote workforces, insulating apps, endpoints and containers from emerging threats.
Learn moreIn the data center
From legacy systems to mission-critical applications, you need steadfast protection to manage your critical on-premises data. Commvault offers comprehensive protection and ubiquitous recovery across your data center, with no workload left behind.
Learn moreAcross clouds
As cloud adoption accelerates, your business needs protection that keeps pace. With the industry’s broadest coverage of cloud-native workloads, Commvault seamlessly protects private, public, and multi-cloud environments – in one cyber resilient platform.
Learn morehow we do it
Backup and recover your data everywhere it lives
Elevate your cyber resilience and data protection with Commvault’s cutting-edge capabilities.
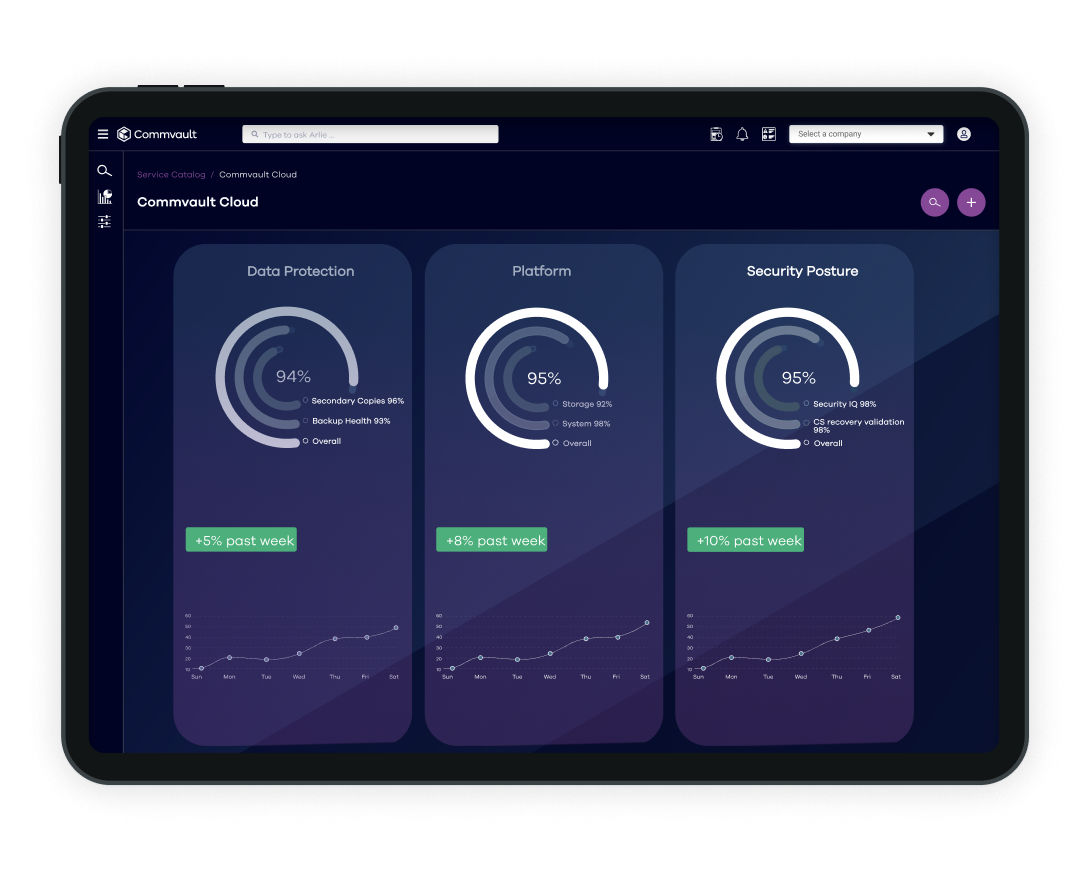
Cleanroom Recovery
Cleanroom Recovery combines unique capabilities to identify and ensure a clean recovery, plus the ability to guarantee safe recovery to a cleanroom in the cloud.
Learn moreAuto Recovery
Actively secure, defend, and recover data in near real-time. Automate the recovery workloads with multilayers data protection.
Learn moreRisk Analysis
Identify, categorize, and classify sensitive data to limit exposure and be compliant.
Learn moreCustomer story
SriLankan Airlines Case Study
SriLankan Airlines integrated Commvault Cloud Backup & Recovery Software, eliminating tape operations and improving data recovery. The airline achieved improved backup windows and data management efficiency. Automation of backup processes saved time and reduced human errors.

Our Reach
Supporting more than 100,000 companies
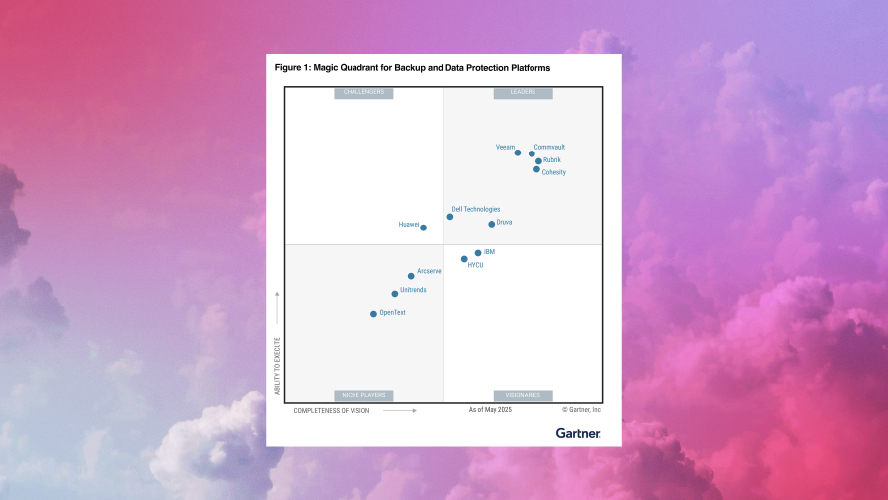
Gartner® Magic Quadrant™

Proactive Defense From Tomorrow’s Cyberthreats

Commvault® Cloud Backup and Recovery
Ready to get started?
Get your free demo
See how easily Commvault’s cyber resilience solutions can protect, defend, and ensure uninterrupted access to your data.






