Ransomware breaches have increased by 13% – more than the last five years combined.1 Sixty percent of InfoSec leaders agree that ransomware threats should be prioritized to the same level as terrorism.2 A cybersecurity attack will impact your organization. It all comes down to how well you have prepared for your cyber recovery.
- Are your organization and employees prepared for a cyberattack?
- Do your teams know their roles, and will they work together?
- Who has the authority/decision-making power to make time-sensitive decisions such as shutting down servers or networks?
- As an executive, are your business leaders in sync, and how will you keep them informed?
Zero Loss Strategy
Consider if a ransomware attack hit you today. Would you have a job or company tomorrow? You need a solution that expands beyond zero trust principles to better plan, manage and reduce the impact of a ransomware attack—introducing Zero Loss Strategy, built on Zero Trust Principles and implemented through a multilayered security framework for consistent and automated data protection and recovery. With Commvault, protect what matters most through the broadest workload coverage for greater data protection and rapid recovery across cloud and storage platforms all through a unified customer experience helping you to remain vigilant against cyber threats. Zero Loss Strategy delivers:
End-to-end data visibility
Catch threats before they fully impact your data. With a single management platform, identify business-critical and sensitive data, reduce your attack surface, and minimize risk exposure.
Broadest workload protection
Protect what matters most. Commvault covers the broadest of workloads, from traditional on-premises to hybrid cloud and SaaS applications; we also support native cloud integration, so as your organization and data grow, we can easily help you scale.
Faster business response
Speed and accuracy are essential to responding to a ransomware attack. Consolidating your data protection to a single dashboard, the Commvault Command Center™ gives your organization greater production and efficiency.
Zero Trust Principles
Trust but verify. Organizations need to follow zero trust principles to ensure cyber threats do not have unlimited access within their networks. It is core to every organization’s proper cyber hygiene.
A Zero Loss Strategy is built on Zero Trust Principles and implemented through a multi-layered security framework. Commvault uses these as the foundation for a Zero Loss Strategy. We provide multiple layers of authentication controls to stop malicious actors, insider threats, and even unintentional accidents from deleting backup data.
Commvault Multilayered Security Protection
Many experts recommend having a layered anti-malware and ransomware strategy. Commvault has built these security capabilities into our data protection software and policies without the incremental management overhead. Commvault data protection and management platform include five security layers:
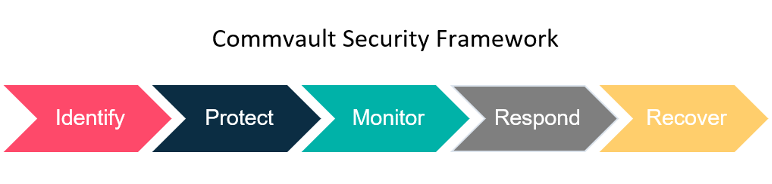
- Identify and mitigate risks to backup data within a single interface
- Protect by applying security controls based on industry-leading standards
- Monitor for ransomware, insider threats, and other threats
- Respond and take action on threats and continuously validate backup data
- Recover data quickly across multiple on-premises, cloud, and hybrid environments
Implement an Action Plan
To help you better protect and manage your data, maintain healthy business operations, and manage risk, you need an approach that brings together your data management teams, security teams, and stakeholders. You need a strategy to help you be better prepared and have the ability to recover quickly if a cyberattack does occur.
- Create an incident response plan and test, test, test
- Ensure you have the right staff, vendors, process and technology in place
- Follow the NIST multilayered security framework: identify, protect, monitor, respond and recover to cover security gaps that may exist in your infrastructure
- Follow Zero Trust Principles to verify those users already in your perimeter
- Use a centralized management system, not multiple product points, for easy visibility across your data
- Eliminate gaps in your environment through air gap, honeypots and isolate networks
Ensure your data protection provider can easily scale with your evolving needs and that you have flexible restore options to rapidly recover. You want a comprehensive approach, not a complex one. Learn more about a Zero Loss Strategy and ransomware protection and recovery.
References
1. InfoSecuity, Benjamin David, Ransomware Attacks Increasing at “Alarmin” Rate, May 2022 – 2. TechRadarPro, Anthony Spadafora, IT Workers Believe Ransomware is as Serious as Terrorism, January 2022.


