The world around us is changing rapidly where everything is being offered and consumed as a Service – including Ransomware. Ransomware as a Service (RaaS) is proving to be the “virus” (pun intended) that is forcing the evolution of security postures adopted by organizations.
Organizations are in varying stages of their journey to cloud, which is being made more challenging by bad actors and threat vectors. Add to this the concerns around misconfigurations in cloud that market analysts have declared as one of the key vulnerabilities that bad actors tend to exploit first.
In the current IT climate, with the ransomware threat looming large, Zero Trust architecture has become central to all enterprise’s security posture. “Challenge and Verify” all communication and access paths between components of the IT landscape is the core tenet of a Zero Trust architecture, which, when available on an easy-to-consume platform, makes it a compelling proposition.
Zero Trust architecture is a shift in paradigm from the concepts of “persistence” of connection that we have seen in the past. It starts with laying the foundations for micro-segmentation of the IT landscape, access limited with the Least Privilege principle, and all communication to and between the micro-segments being authenticated, audited, and verified. Leveraging micro-segmentation helps create micro-containment zones in the event of a disaster to minimize the lateral movement of threat vectors.
However, despite best-laid plans, we witness organizations falling victim to ransomware attacks and being subject to double extortion. In such cases, an organization’s ability to minimize business downtime relies heavily on its secure backup copies and recovering safely, at optimal speed, performance, and cost. This is proving to be the insurance policy that customers are relying on.
Constantly in step with the changing times, Commvault, armed with 25 years of experience in the data protection and management arena, helps customers recover their data and bounce back from cyber and disaster recovery (DR) crises via a multi layered security approach. These success stories only go to highlight the importance of backup copies that are cyber- and recovery-ready!
To be able to bring all siloed workloads – reducing the surface area of attack, into a unified framework that can easily fit into customers current hybrid ecosystem, with on-premises and SaaS presence, and consistently deliver the highest level of protection and recovery assurance at every layer of interaction, is now the gold standard in cyber-recoverability.For Commvault, adhering to business SLAs is of the highest priority and a non-negotiable parameter.
Across our Intelligent Data Services Platform, customers have a wide range of options to support their workloads and deployment flexibility. Commvault customers enjoy a seamless experience of protecting and managing data across on-premises, cloud, and SaaS platforms.
- Commvault HyperScale X is Commvault’s hyperconverged infrastructure (HCI) offering leveraging Commvault Distributed Storage. Customers benefit from uniformly high standards of security, segmentation, and ease of deployment. HyperScale X also benefits the customer with seamless cloud integration options.
- Metallic Cloud Storage Services (MCSS) is a Commvault/Metallic flagship offering built on Azure services. Metallic Hub provides SaaS flexibility for Microsoft Office 365 and Salesforce.com, apart from several other cloud-centric workloads. Similarly, Metallic Cloud Storage services complement hybrid use-cases of enterprise customers looking for the much-needed logically segmented and air-gapped data of a secondary or tertiary copy. MCSS storage provides customers the peace of mind and the assurance that, with the abstraction of access and additional security layers, complete with data encryption at rest and in-flight, their data is immutable.
With backup copies becoming the “insurance policy” for enterprises to recover from, data immutability is critical.
Customers have an array of capabilities built into Commvault software that complement anomaly detection and notification mechanisms, making it a secure and cyber-ready data protection solution. As described by the NIST Cybersecurity Framework, enterprises are fast aligning themselves to the “Defense in Depth” strategy. When extended to data protection and management environments, the same framework helps achieve desired levels of immutability and security without compromising recovery, performance, and cost.
Best Practices for Security and backup data immutability
Immutability is defined as the ability of any data to be maintained in a non-fungible state for a specific duration of time. Data immutability can be attained via various methods working in conjunction with each other.
Here are the key best practices recommended by Commvault to achieve security and backup data immutability:
1. Have a tighter grip on Role-Based Access Controls to ensure only resources within the organization have access to backup repositories. Coupled with multi-factor authentication (MFA) and Multi-person authentication, this ensures protection against rogue admin or compromised admin credentials. Answering basic questions like “Who has access to what and why?” helps guide the Role-based Access Control (RBAC) principles. This aligns with Least Privilege Access guidelines.
2. Protect against “rogue admin” or “compromised admin credentials” wreaking havoc on your Commvault environment by enabling Commvault Retention Lock on the policies (formerly known as WORM Copy). Once enabled on a policy, this software level locking configuration helps protect against accidental or intentional deletions or changes to the policy retention, deleted jobs or unmounted/dropped libraries, by anyone including admins.
3. Encryption is a default setting for Commvault. Data at rest and in-flight is encrypted and assures the backup data, even if exfiltrated, is rendered useless to bad actors without the decryption keys. Additionally, since data written by Commvault is in deduplicated chunks, the blocks of data are not of any use to bad actors in the event of Double Extortion Ransomware threats.
Commvault’s integration with and support for 3rd party Key Management Servers provides an additional layer of security.
4. Commvault’s Ransomware Lock protects on-premises data mover mount paths, wherever relevant. This ensures data can be written into the target disk storage only by Commvault and Commvault approved processes, thus rendering the mount path inaccessible to read, writes, and updates any non-Commvault process, hence immutable.
5. With Commvault HyperScale X, customers gain tighter OS-level data protection that blocks users and/or ransomware attacks from bypassing other security layers through access controls. Under the hood, HyperScale X engages SELinux to enhance immutability by providing access policies restricting file modifications or disk-level activity, such as reformatting drives. Most importantly, HyperScale X powered by Commvault’s integrated scale-out file system provides additional immutability at the storage layer. This ensures that data in backup repositories cannot be modified or encrypted at the file system level. This capability is enabled by default.
6. Access to cloud storage services is authenticated just before backup jobs are triggered. This also aligns closely with Zero Trust architecture, which mandates all communication channels be “Challenged” and then “Verified,” thus negating the notion of persistence.
7. Commvault also allows leveraging time–based retention lock (WORM immutable lock) on Cloud Object storage and on-premises object storage that support it. Backup copies placed in cloud storage, where a time-based retention lock is applied, cannot be deleted or updated by any process or persons, including Cloud IaaS vendors until retention is met.
8. Network topologies recommended by Commvault emphasize “Pull” architecture vs. “Push” thus, adhering to the principles of Zero Trust architecture. Push architecture relies on the persistence of connection and has the potential for malware to infiltrate through this always-on connection; however, in “Pull” architecture, connection to the clients is periodic, which requires a request for access, authentication of access, and finally resulting in “pulling” of data and events.
9. For Metallic Cloud Storage Services, the Metallic storage subscription is abstracted away from the customers, as they have visibility only to their Metallic Storage account and not the Metallic subscription. This layer of abstraction, when used in conjunction with Commvault Retention Lock, provides a secure and immutable copy of data on MCSS.
Key Architecture Considerations for Immutability
One of the frequently asked questions is, how do we architect the right fit for a given environment with all these capabilities? What are the key architecture considerations when designing a hybrid environment while balancing security, cost, and performance parameters?
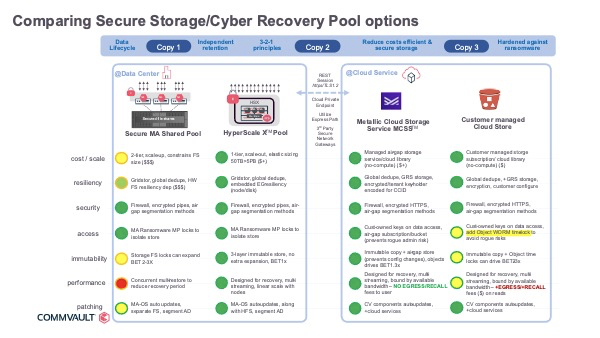
Include these elements in your immutability architecture
- Access locks to isolate copy store against Ransomware
- Immutability with lifecycle locks to reduce risks, balanced with consumption impact
- Air-gap isolation network and controls
- Configuration governance to protect against intentional or accidental changes
- Recovery concurrent performance – reduce latency with due importance to speed and cost impact
- Automatic patching to stay current, simplifying management and maintenance of data protection infrastructure
- 3-2-1 Offsite vaulted copy
The image below illustrates these salient points that can serve as a quick and easy guide.
To learn more about Commvault immutability, read Commvault’s immutable infrastructure architecture.


