Reduce Risk to your Sensitive Data
Identify, categorize, and classify sensitive data to limit exposure and help comply with privacy requirements.

Demo Video
Commvault® Cloud Risk Analysis
See how Commvault® Cloud Risk Analysis can help organizations implement data risk governance processes.

How we do it
Reduce risk and defend sensitive data
Identify your sensitive data and define automated policies to secure and manage your data correctly throughout its lifecycle.
Minimize your data attack surface
Identify and classify sensitive files across multiple data sources, on-prem or in the cloud, and apply retention, archive, or deletion policies.
Help comply with regulations
Manage access permissions and identify overexposed data to bolster privacy.
Save money on storage costs
Archive or delete redundant, obsolete, and trivial (ROT) data to lower your storage cost and improve backup performance
Manage data risk
Reporting on data sensitivity, location, and owners helps make better informed data management decisions.
Classify data for ease of governance
Easily search, find, tag, hold, or delete data for legal, compliance, or data lifecycle management.
Assess threats and secure data
Drill down into file anomalies or other risk factors to proactively quarantine or delete affected files.
RISK ANALYSIS features
Intuitive data governance to reduce data risks
Discover, classify, and control your data to minimize risk and your attack surface.
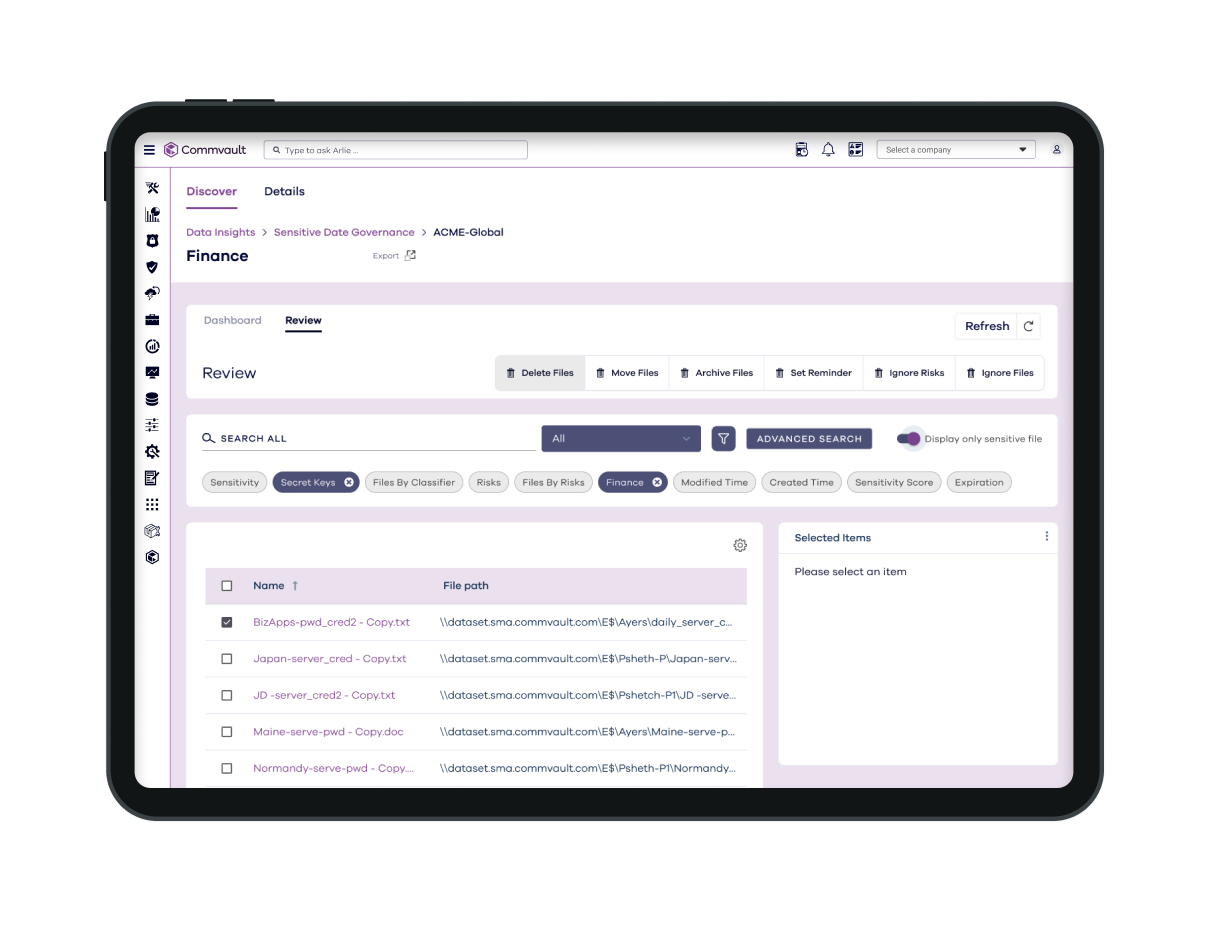
INTELLIGENT DATA DISCOVERY
Automatic discovery across live and backup environments
Find and classify sensitive data, such as customer PII, company intellectual property, or confidential secrets, like API keys.
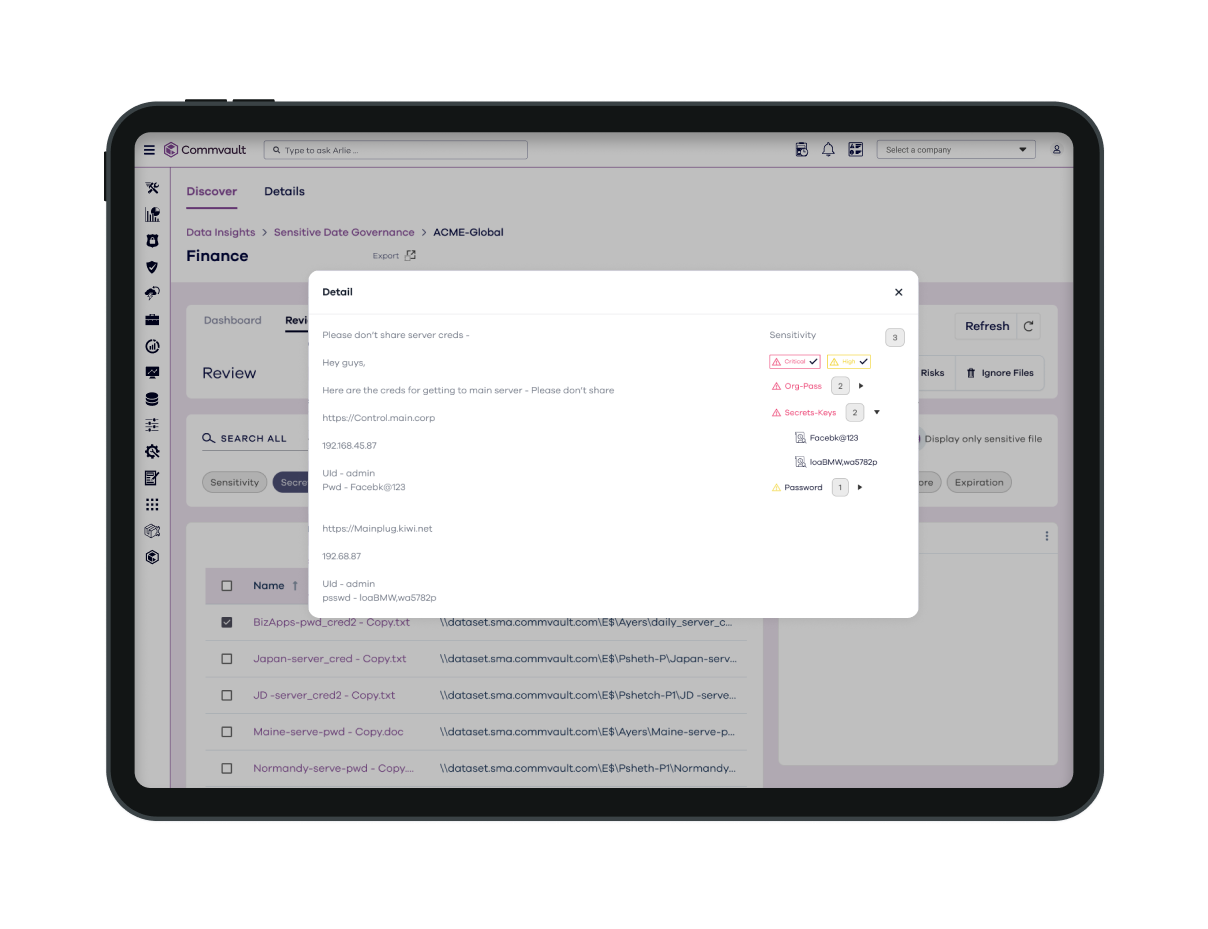
CONTROL AND GOVERNANCE
Apply data governance policies
Classify data and apply policies that help restrict access or sharing, or manage its lifecycle for retention, archiving, or deletion.
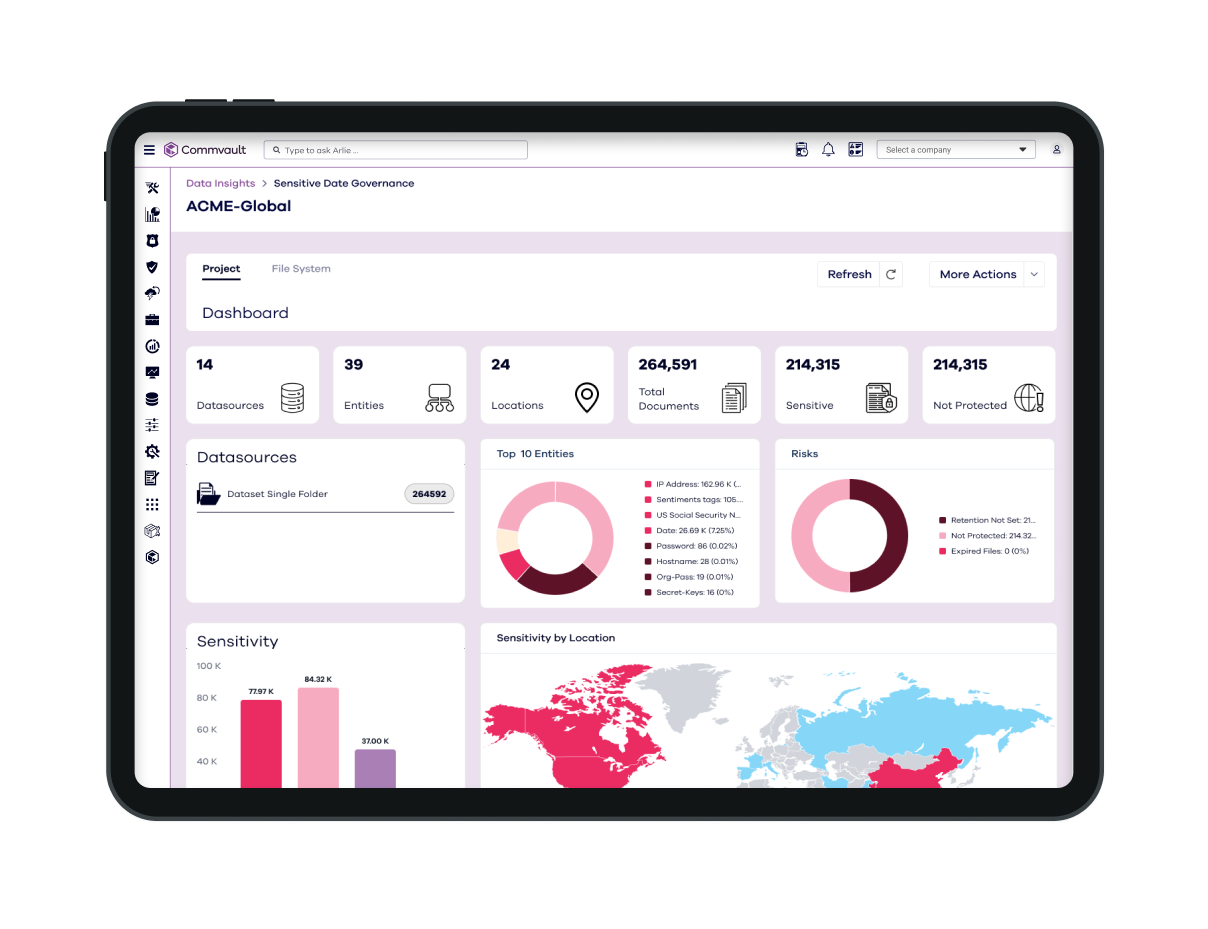
DATA LIFECYCLE MANAGEMENT
Automate data retention and disposal
Reduce your attack surface and storage bill by automatically deleting ROT or unused data.
Analyst Report
Gartner® Magic Quadrant™
For the 14th time in a row, Commvault has been named a Leader in the Gartner® Magic Quadrant™ for Backup and Data Protection Platforms.

Our Reach
Supporting more than 100,000 companies
Datasheet
Commvault® Cloud Risk Analysis
Gain visibility into data risks to secure and defend sensitive data and improve your security posture.


Risk Analysis product overview

Streamlining data protection and management for the hybrid enterprise

Modern security strategies
Frequently Asked Questions
Can I use Risk Analysis to help me understand over-permissioned or overexposed access?
Yes, excessive permissions can be discovered during the data discovery process, and unprotected or overexposed data can be highlighted for remediation.
How does Risk Analysis help reduce my risk?
Sensitive data must be known and controlled to help comply with data management best practices and privacy regulations, like GDPR and CCPA. Once known, you can validate that appropriate access controls and lifecycle event policies, like retention or deletion, are applied and followed.
Can I use Risk Analysis to search for any kind of data, or just sensitive data?
Risk Analysis can be configured to search metadata or full file data, including its contents. File contents can be indexed to allow for general searching, and images can be made searchable with OCR capabilities within Risk Analysis.