Drive Down Risk & Simplify Data Compliance
Remediate risk, limit exposure, and meet stringent compliance standards across all data environments.

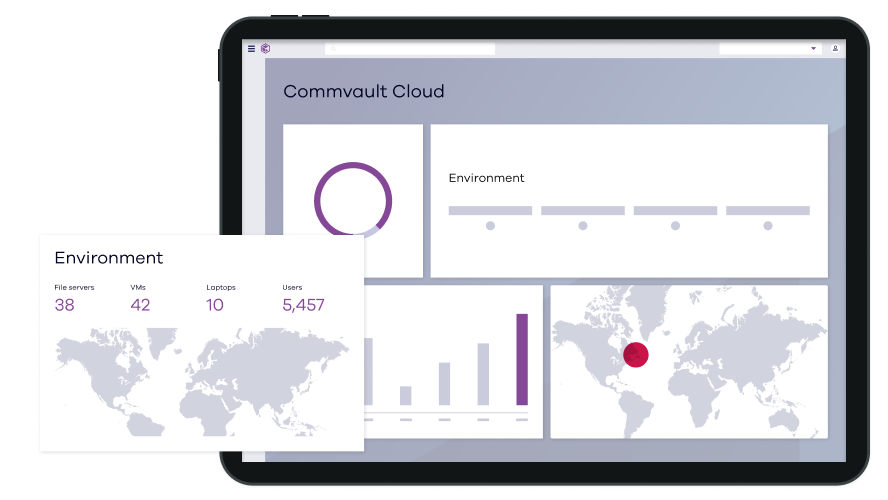
Manage governance, risk & compliance
Proven performance meets trusted compliance. With Commvault® Cloud you get next-generation cyber resiliency with the insights and reporting required to meet governance, risk and compliance standards.
Risk of incorrect data handling
6M
Number of data records exposed worldwide during Q1 20231
2.6x
The cost of noncompliance vs. the cost of maintaining or meeting compliance standards2
$5.87M
Average revenue loss due to a single noncompliance event3
1Data records breached worldwide 2023 – Statista. 2Ponemon Institute – The True Cost of Compliance. 3Jeff Purrington Saviynt The True Cost of Non-Compliance, May 2022.
Governance and compliance baked-in
Minimize exposure and maintain data compliance.

City of Everett secures Office 365 data and makes eDiscovery 3x faster
Learn how city officials increased efficiency and compliance with Commvault.
Introducing
Commvault® Cloud
The only modern data protection platform reimagined from the ground-up to solve the challenges of the hybrid world.

Metallic® AI
Metallic AI is the engine that powers Commvault Cloud. With intelligent management and control along with a powerful mix of ML and automation.